Facebook promises to share details of stolen account information with 30 million affected users in coming days

Facebook also shared details about the attack that it found exploiting a vulnerability in the ‘View As’ feature of the platform. The social network clarified that not 50, but 30 million Facebook users had their tokens stolen.
Facebook has issued an update on the previously reported hack in which the company had estimated that accounts of nearly 50 million people were compromised after cybercriminals used a flaw in the platform’s ‘View As’ feature. According to an official statement from Facebook, tokens of about 30 million people were actually stolen. The company also shared the details of the attack that exploited user data.
“We have been working around the clock to investigate the security issue we discovered and fixed two weeks ago so we can help people understand what information the attackers may have accessed. Today, we’re sharing details about the attack we’ve found that exploited this vulnerability. We now know that fewer people were impacted than we originally thought. Of the 50 million people whose access tokens we believed were affected, about 30 million actually had their tokens stolen,” Guy Rosen, Vice President of Product Management, said in a blog post.
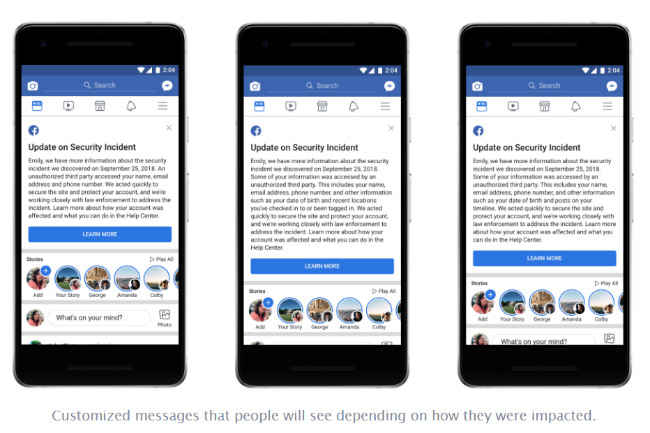
Facebook also said that the attack did not include Messenger, Messenger Kids, Instagram, WhatsApp, Oculus, Workplace, Pages, payments, third-party apps, or advertising or developer accounts. The company also said that in the coming days, it will send customised messages to the 30 million people affected to explain what information the attackers might have accessed, as well as steps they can take to help protect themselves, including from suspicious emails, text messages, or calls.
According to Facebook, attackers exploited a vulnerability in Facebook’s code that existed between July 2017 and September 2018. The vulnerability was the result of a complex interaction of three distinct software bugs and it impacted “View As,” a feature that lets people see what their own profile looks like to someone else. It allowed attackers to steal Facebook access tokens, which they could then use to take over people’s accounts. (Access tokens are the equivalent of digital keys that keep people logged into Facebook so they don’t need to re-enter their password every time they use the app.)
Facebook said that it saw an unusual spike of activity that began on September 14, 2018 and on September 25, it determined that the activity was actually an attack. The company claims that it identified the vulnerability and within two days, it closed the vulnerability, stopped the attack, and secured people’s accounts by resetting the access tokens for people who were potentially exposed. In a precautionary move, the social media platform also turned off “View As.”
How hackers executed the attack
Facebook claims that the attackers already controlled a set of accounts which were connected to Facebook friends. They used an automated technique to move from account to account so they could steal the access tokens of those friends, and for friends of those friends, and so on, totaling about 400,000 people. In the process, however, this technique automatically loaded those accounts’ Facebook profiles, mirroring what these 400,000 people would have seen when looking at their own profiles.
“If a person in this (compromised) group was a Page admin whose Page had received a message from someone on Facebook, the content of that message was available to the attackers. The attackers used a portion of these 400,000 people’s lists of friends to steal access tokens for about 30 million people. For 15 million people, attackers accessed two sets of information – name and contact details. For 14 million people, the attackers accessed the same two sets of information, as well as other details people had on their profiles,” Rosen explained in the blog.
The ‘other details’ included username, gender, locale/language, relationship status, religion, hometown, self-reported current city, birthdate, device types used to access Facebook, education, work, the last 10 places they checked into or were tagged in, website, people or Pages they follow, and the 15 most recent searches. For 1 million people, the attackers did not access any information.
The update comes a few days after the company disclosed that a Facebook bug had erased Live videos of some of the platform’s users. The glitch deleted some users’ Live videos if they tried to post them to their Story and the News Feed after finishing their broadcast. The company later patched the bug, but said that it could only restore some of the deleted videos and was seen issuing an apology notifying the affected users that their Live videos have been deleted permanently.
Cover Image: Facebook
Digit NewsDesk
Digit News Desk writes news stories across a range of topics. Getting you news updates on the latest in the world of tech. View Full Profile