Hidden Threat: NTFS Alternate Data Streams (ADS)
So what’s so special about ADS?
One may think, “A text document’s summary is stored as ADS… so what?” Well, there’s more to it — executable code can also be stored as an alternate data stream without the Timestamp, listed File’s size or running process name being modified. Moreover, files with ADS are almost impossible to be detected by native file browsing techniques like Windows Explorer or the command line; software that can identify them are few and far in between…
 Survey
SurveyExploiting ADS
The lengths a malicious hacker can go to hide his tracks can be astonishing, and this is what makes ADS the worst nightmare of a System Administrator. Due to the concealed nature of ADS, detecting and preventing execution of malicious code is intricate.
Once a hacker has acquired administrator access on the system, he’ll strip off all information of concern, covering the detection of his presence and will try to install a backdoor (a remote access Trojan) for easy future access. This backdoor needs to be veiled from the system administrator, this is where ADS comes to in – it can be used to hide files on the breached system, evading detection and executing them without the knowledge of the sys admin.
The ability to hide executable code in an invisible form inside ADS can also make viruses difficult to be detected within a file system, because most virus scanners only verify the default data stream of files. Major Anti-virus vendors point out that ADS must be loaded into the memory before execution and thus will be detected with real-time scanning (when a file is scanned after it is loaded in memory (just after commanded to execute), the type of scan is known as a “real-time” scan). The problem with this approach is that many network administrators do not run real-time scanning on their servers or workstations due to performance issues.
Denial of Service (DoS) attacks that exploit the use of ADS also exist. It is the difficulty of detection that increases the threat. For example, it is quite common for an attacker to create a file large enough to fill up the system partition on a Windows NT/2000 system, to crash the server due to lack of space for temporary files. When using the main stream of a file in such an attack, the violating files are easily identified due to their abnormally large size. By using Alternate Streams here, it can be made difficult to detect where the violating files are located on the system. Another attack exploiting ADS can be launched by creating a large number of alternate streams, more than 6,000 on a specific file. If the attacker or the system tries to access the default stream of the file, the system’s response slows considerably and in worst case, the system crashes thus creating a Denial of Service.
Moreover, this vulnerability is not confined to the NTFS file system; any other file system that uses streams for alternate data is vulnerable.
Challenges
Let’s make one
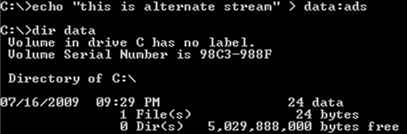
1. We have created a file named “data” in C: root directory containing the text “this is main stream.” This text is stored in default or main stream of the file. Notice that the file size is 24 bytes.
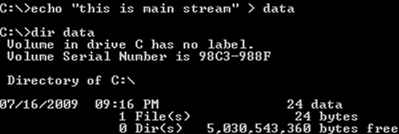
2. Next, We create an ADS — adding the text “this is alternate stream” to the existing file “data”. The syntax for this function is <filename>:<alternate stream name>. Notice that the alternate stream does not show up in the root directory; the file size remains intact (24 bytes).
Countermeasures
ADS is a not a feature that can be disabled, so countermeasures are quite important.
- Antivirus, The best practice is to enable real-time scanning. As mentioned earlier, real-time scans can certainly shield from execution of a malicious code inside an alternate stream.
- File Monitoring, monitoring changes to the file system helps to detect the creation of additional or new data streams. Many freeware tools are available for monitoring NTFS partitions for Alternate Streams. Some of them are listed below:
LADS (List Alternate Data Streams) (http://www.heysoft.de)- Marx NTFS ADS Viewer (http://www.softpedia.com/progDownload/Marx-NTFS-Alternate-Data-Streams-Viewer-Download-50793.html)
- Streams (Sysinternals) (http://www.sysinternals.com)
- NT Objectives Forensic Toolkit (http://www.ntobjectives.com)
A commercial product, Tripwire (www.tripwiresecurity.com) is also available. It automatically audits your file system for changes, access and ADS. Being a commercial product, it provides excellent protection against attackers using ADS to hide their activities on systems. But it serves as a notification tool only and you need to personally verify if the Alternate Data is legitimate or whether it needs to be deleted manually.
- Backup: There are some commercial software that provide backup functionality for handling ADS
- Symantec Backup Exec (earlier, Veritas Backup Exec) (http://www.symantec.com)
- AISBackup (http://www.aiscl.co.uk)
- Backup Express (http://www.syncsort.com)
- NetWorker 5.51 (http://www.legato.com)
Conclusion
The article targeted ADS as a vulnerability, rather than a compatibility feature, but it’s important to realize that ADS is an essential part of NTFS and has legitimate uses too. In the end, the security features of NTFS far outweigh this vulnerability. With knowledge and due diligence, administrators can take actions to prevent and detect unauthorized use of ADS and protect themselves adequately.
References:
securityfocus.com