Everything you need to know to become a cloud security engineer

Cloud technology, just like other prominent fields of tech such as AI, ML and big data, is growing exponentially year after year. Cloud computing brings limitless computing resources, drastically changing how industries, such as IT, function at their core. As cloud computing grew, three prominent names emerged in this burgeoning field – AWS (Amazon Web Services), Microsoft Azure, and Google Cloud. The growing vendors in this market also drove intense competition. New, emerging technologies such as serverless, containers, microservices, blockchain, and more, all spun from the cloud or closely operated with it.
 Survey
SurveySo, why do we need security on the cloud? And why can’t we use traditional network security solutions? Well, traditional network security only makes sense when all the apps are hosted in the data centre and the users are all on the network. However, this has completely changed due to the inception of the cloud. Users and businesses have tremendous amounts of data backed up on the cloud, so it is integral that their (possibly) sensitive data must be kept safe. A set of policies, controls, procedures and technologies must be developed to protect cloud-based systems, data and infrastructure. This is where cloud security engineers or specialists come in.
What is cloud security?
As touched upon above, cloud security is a set of strategies and practices developed to protect data and applications hosted in the cloud. There are a wide variety of attacks that can occur in the cloud, therefore cloud security attempts to encompass numerous kinds of possible attacks. A well-designed cloud security strategy can vastly diminish the risk of cyberattacks.
Note: cloud security is different from SaaS or SECaaS (Security as a service). The latter refers to the security products that are hosted in the cloud.
Some of the main cloud security risks include data being exposed or leaked, unauthorised user access, an authorised user having excessive access to data, and malicious attacks such as DDoS attacks or malware infections. An efficient cloud security strategy would attempt to significantly reduce the threat posed by these risks by protecting data, managing user authentication and access to data, and staying operational even during an attack.
key technologies associated with cloud security
A cloud security solution must incorporate certain key technologies that are important in the world of the cloud. It would help any aspiring cloud security engineer to familiarise themselves with these processes. The following technologies are the common ones –
Encryption: A method which involves scrambling data around so that only the authorised parties can actually understand the haywire information. Chances are that hackers that find their way into a company’s cloud will have a significantly tougher time carrying out a number of malicious acts, such as leak, sell or misuse the data, if it has been encrypted. The hacker will come across the scrambled data which cannot be used unless the decryption key is discovered, which is (almost) always impossible.
In the cloud, data can be encrypted at rest (when stored) as well as when in transit (when it is sent from one place to another). Ideally, the data should be encrypted both times to prevent hackers from intercepting the data and accessing it. Also, data in transit includes both data travelling from the cloud to a user, and data travelling from cloud to cloud (multi-cloud or hybrid cloud environment). So, encryption should be performed during both kinds of transfers.
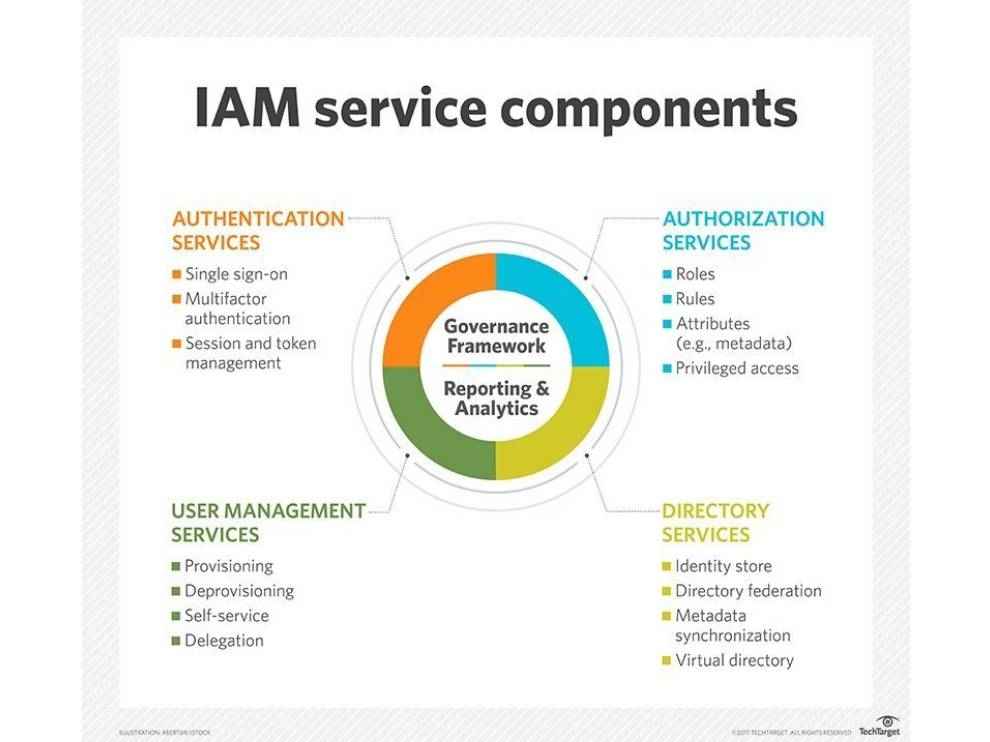
Identity and access management (IAM): Identity and access management products track the user and what exactly they are allowed to access. In accordance to this, IAM products either authorise users or deny access to unauthorised users as deemed fit. IAM is extremely important in cloud computing since the user’s identity and access privileges dictate whether a user can access the data, not their device or location. IAM solutions are especially effective against account takeovers and insider attacks. IAM solutions usually include several services (separate or all-in-one) such as identity provider (IdP), single sign-on (SSO), multi-factor authentication (MFA), access control services and more.
Firewall: A cloud firewall provides protection around cloud data by blocking malicious traffic on the web. Cloud firewalls are hosted within the cloud and act as virtual barriers around the cloud infrastructure. Cloud firewalls prevent DDoS attacks, malicious bots and other vulnerability exploits.
What does a cloud security engineer do?
A cloud security engineer or a cloud security specialist specialises in providing security for cloud-based platforms and plays an important role in safeguarding a cloud-based organisation’s data. A cloud security engineer’s role often entails analysing existing cloud structures and attempting to come up with new, enhanced security solutions.
A typical cloud security engineer is expected to have a thorough understanding of the technologies we discussed in the previous section. In addition to those, they must also understand how to properly configure security settings for cloud servers to avoid exposed data. They must also perform threat simulations to detect possible risks and flaws in the cloud-based security programs of the organisation. Depending on the result of these simulations, cloud security engineers must be able to provide astute recommendations to improve security. It is their job to not only create security technologies for the cloud but also investigate, recommend and educate (users as well as employees). A cloud security engineer must also ensure consistency in the security policies and measures they implement across a company’s infrastructure including public clouds, private clouds and on-premises infrastructure. If there are any inconsistencies, hackers will find it easier to target it.
Qualifications and skills required
Prospective candidates aspiring to become cloud security engineers must at least have a bachelor’s degree in fields such as computer science, programming, or information security. However, some firms do require a master’s degree. Aspirants can also pursue certification through the Cloud Security Alliance (recently opened up its second Chapter in India) or the (ISC) ².
Cloud security engineers need to possess strong technical skills such as experience with Windows OS or Linux, languages such as Python, micro-service development using Java and Node.js, knowledge of DevOps and DevOps tools and experience with cloud providing ecosystems such as AWS. Additionally, extraordinary attention to detail can help them succeed since they have to keep monitoring cloud systems to pick up on risks and threats.
Scope for the future
According to a 2018 report by edtech platform, Great Learning, India is expected to see a massive rise in cloud computing jobs by 2022, thereby significantly increasing the demand for cloud security engineers. As more and more organisations are beginning to shift their operations to the cloud, the Indian cloud computing market is expected to grow to $4 billion by the end of 2020. The field has also recorded an annual growth rate of over 30 per cent.
The prospects for cloud security engineers are bright since cloud engineers get paid a much higher salary package than traditional IT services roles in India, with entry-level salaries varying between `5 lakh to `7 lakh per annum. Also, cloud engineers with about 5 years of experience typically begin earning between `12 lakh to `19 lakh per annum. The cloud computing industry, not only in India but the entire world, witnesses a severe dearth of talent with over 1.7 million cloud jobs remaining vacant worldwide. According to IDC data, there is only one qualified candidate for every 100 job postings in cloud computing. Therefore, the need for skilled and talented cloud engineers is growing rapidly in India since the technology is also spreading its reach further in the country.
Dhriti Datta
Perpetually sporting a death stare, this one can be seen tinkering around with her smartphone which she holds more dear than life itself and stuffing her face with copious amounts of bacon. View Full Profile