How 1.3 billion passwords were stolen: Infostealer malware data breach explained
1.3 billion passwords leaked via infostealer malware: what happened
Troy Hunt clarifies 2 billion email leak isn’t Gmail breach
Protect accounts from data leaks with passwords, 2FA, and passkeys
In one of the largest data leaks ever recorded, cybersecurity researchers have uncovered a database containing over 1.3 billion unique passwords – a staggering amount that underscores the fragility of online privacy today. The discovery isn’t tied to a single breach or hack. Instead, it’s an aggregation of years’ worth of stolen data harvested from millions of computers infected by infostealer malware.
 Survey
SurveyInfostealers are a category of malicious software designed specifically to extract saved login credentials, cookies, autofill data, and other sensitive information from infected systems. Once deployed, often through phishing emails, fake downloads, or pirated software, they silently copy stored data from browsers and applications, sending it back to the attackers. These stolen credentials are then compiled, sold, or leaked on the dark web and underground forums.
Also read: AI meets storytelling: My experience at the Mumbai AI Film Festival (MAFF)
This latest leak, dubbed by some researchers as a “mother of all breaches,” combines data from multiple smaller leaks and malware logs over the past decade. The structured format of the files – listing websites, usernames, and corresponding passwords – makes them dangerously accessible to anyone who finds them online. What’s worse, most of the stolen credentials belong to popular global platforms like Google, Apple, Facebook, Telegram, and banking services, meaning billions of users worldwide are potentially affected.
This has been an extraordinary set of data to process: 1.3B unique passwords, 2B unique email addresses (including mine 😭) and almost 3M of our @haveibeenpwned subscribers in there. It’s been weeks of processing to get this loaded, and finally, it’s done https://t.co/f5okTCYstn
— Troy Hunt (@troyhunt) November 6, 2025
Adding context to the scale of this exposure, Troy Hunt, creator of Have I Been Pwned, confirmed that the new dataset also contains nearly 2 billion email addresses, including 394 million unique Gmail accounts. However, he clarified that this is not a Gmail breach. “Eighty percent of the data has absolutely nothing to do with Gmail,” Hunt said, “and the 20 percent that are Gmail addresses have absolutely nothing to do with any sort of security vulnerability on Google’s behalf.” In other words – your Gmail isn’t hacked; your computer might be.
How Infostealers Work
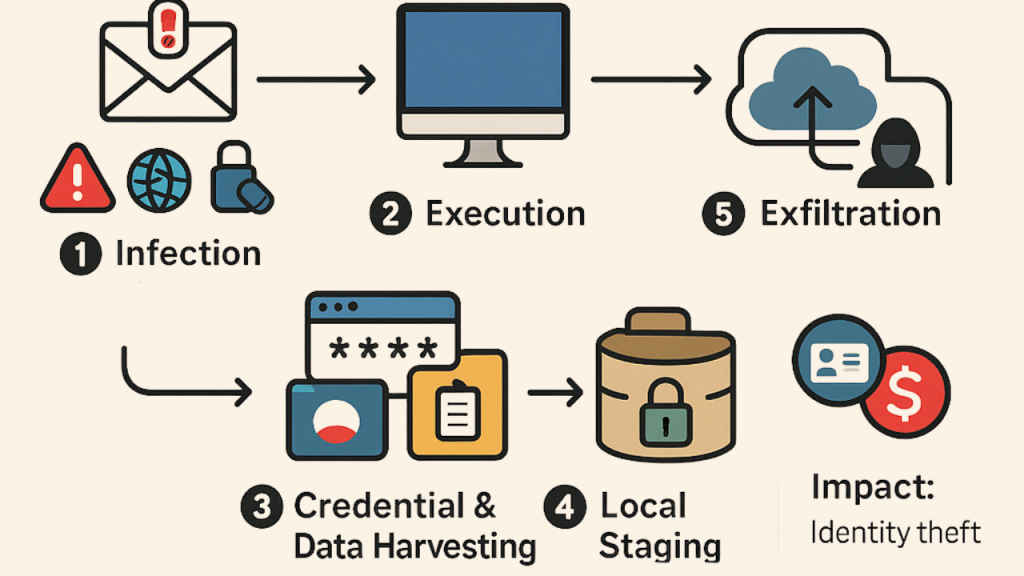
Infostealer malware often hides in plain sight. Victims typically download it disguised as a game mod, a cracked app, or even a browser extension. Once installed, it executes silently, scraping local data files that store your credentials. Unlike ransomware, which announces its presence, infostealers are built to stay undetected for as long as possible, maximizing the amount of data collected before being removed or discovered.
According to cybersecurity experts, much of the data in the 1.3 billion-password leak originated from malware families like RedLine Stealer, Raccoon, and Vidar, some of the most notorious infostealers in circulation. These tools are sold cheaply on underground marketplaces, sometimes for as little as $10 to $20, making it easy for even low-skilled attackers to participate in credential theft operations.
Also read: Mustafa Suleyman’s AI plan for Microsoft beyond OpenAI: What it means
The result? A sprawling web of compromised data that keeps resurfacing in new “mega leaks” as hackers merge and reupload old collections with freshly stolen data.
Remedial measures and best practices
The 1.3 billion-password leak is a brutal reminder that passwords alone are no longer enough to protect digital identities. However, there are several steps users can take to reduce their risk and recover safely:
- Change Your Passwords Immediately – Start with your primary accounts: email, banking, and social media. Use strong, unique passwords for each. Avoid reusing passwords across services.
- Use a Password Manager – These tools can generate and securely store complex passwords, eliminating the need to remember them. Services like Bitwarden, 1Password, and Dashlane work.
- Enable Two-Factor Authentication (2FA) – Even if your password is stolen, 2FA adds a critical second layer of defense. Use an authenticator app instead of SMS where possible.
- Check If You’ve Been Compromised – Use free tools like Have I Been Pwned or Cybernews’ Leak Checker to see if your credentials appear in any breach database.
- Avoid Downloading Cracked or Unverified Software – Many infostealers spread through pirated or “free” versions of popular programs. Always download apps from official websites or trusted app stores.
- Keep Your System Updated – Regularly updating your operating system, browser, and antivirus software ensures known vulnerabilities are patched before malware can exploit them.
- Consider Passkeys – Passwordless authentication methods like passkeys, supported by Google, Apple, and Microsoft, offer stronger security by using cryptographic keys tied to your devices.
A Wake-Up Call for the Internet
This incident isn’t just another statistic, it’s a clear warning. As cybercriminals grow more organized and AI-powered phishing makes deception easier, individuals and organizations must evolve their security habits. The age of single-password protection is over.
The takeaway from this breach is simple yet urgent: trust no device completely, trust no password entirely. The only sustainable way forward is adopting layered digital hygiene – regular password audits, 2FA, and smarter browsing practices.
Because in today’s internet, your password is only as strong as the weakest link that stores it.
Also read: Indian youth are using AI chatbots for emotional support, warn Indian researchers
Vyom Ramani
A journalist with a soft spot for tech, games, and things that go beep. While waiting for a delayed metro or rebooting his brain, you’ll find him solving Rubik’s Cubes, bingeing F1, or hunting for the next great snack. View Full Profile