99.7 percent of Android devices vulnerable to unencrypted Wi-Fi attack

Folks over at Ulm University in Germany have determined that all Android phones running any version below Android 2.3.4 Gingerbread are vulnerable to attacks over unencrypted Wi-Fi networks. And since only the Nexus S, and a few other devices have that update onboard, that pretty much means the entire Android user base (99.7%) is at risk.
 Survey
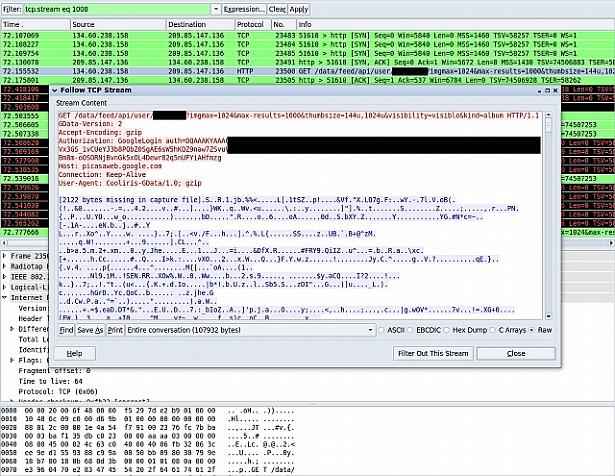
SurveyThe German researchers published their findings in a paper entitled “Catching AuthTokens in the Wild: The Insecurity of Google’s ClientLogin Protocol.” Vulnerability is specific to unencrypted Wi-Fi hot spots, where the team demonstrated an attack that gained access to all items of contacts, calendar events, and private pictures, including those currently being synced. This is done with an impersonation attack, stealing authToken (authentication tokens), markers used to communicate between the Android device and Google services.
[RELATED_ARTICLE]By steal authToken, the hackers can theoretically access a variety of other Google services on the phone, at least those that use ClientLogin authentication protocol for its data APIs. The best solution is to upgrade to Android 2.3.4, but upgrades are hard to come by, with both manufacturers and operators lagging far behind the curve.
All is not so bleak though – switch-off automatic synchronization on your device, and don’t use apps, whenever you log on to unencrypted Wi-Fi. Or in other words, don’t log on to an open Wi-Fi network.
Screenshot of Wireshark showing the authToken for ClientLogin in a data API request to the Picasa Web Albums service.