New Android Trojan can take over PayPal and even bypass 2 Factor Authentication to send money
The new trojan is being distributed via third-party online app stores and fortunately, isn't on the Google Play Store.

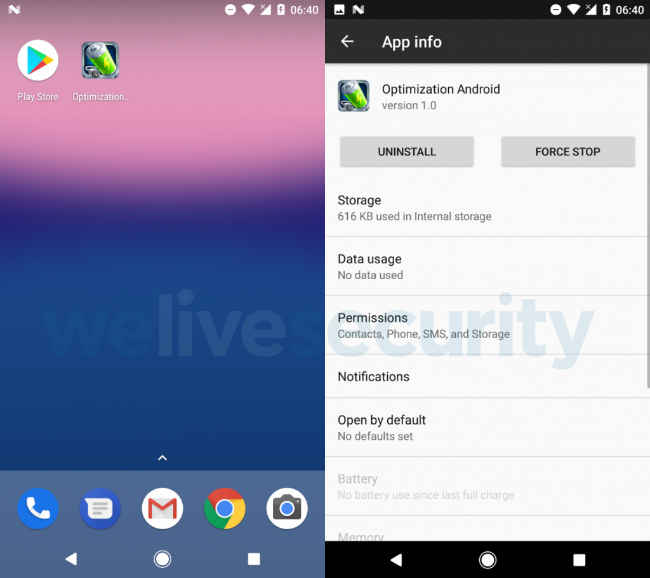
Security researchers at ESET have discovered a new Android Trojan that has the potential to cause considerable monetary damage to users. As per WeLiveSecurity, a new Android malware can steal money from a victim’s PayPal account, even with 2-Factor Authentication (2-FA) turned on. The trojan has been disguised as a battery optimisation app called “Optimization Android,” which is being distributed via third-party online app stores and not the Google Play Store. Once the app is installed and launched, it will boot and close immediately. Then, the user will be requested to grant Accessibility permission, which will give the app complete authority but this process is masqueraded as “enable statistics.”
 Survey
SurveyLukas Stefanko from WeLiveSecurity also posted a video of the trojan in action. In the video below, you will notice that the app sends a notification to the user after it’s installed, which states “Confirm your account immediately.” Tapping on the notification boots up the official PayPal application on their phone and any unsuspecting user would sign-in like they would normally do, even with the 2-FA enabled. However, as soon as the user signs in, the trojan then automatically fast forwards through the money transfer process by emulating taps, which it can do so because of the access to accessibility service. In the video below, you might notice that it automatically sends $100,000 to the attacker’s PayPal address. The malware is said to change the currency used based on a user’s location.
Android Trojan makes PayPal payment on behalf of user.
It sends $1,000 from victim's account every time user opens PayPal app.https://t.co/942rAYv0NT pic.twitter.com/h2fdGui5Y2
— Lukas Stefanko (@LukasStefanko) December 11, 2018
The Trojan takes less than five seconds to automatically send money from the victim’s PayPal account. As per WeLiveSecurity, the process is only halted if the user has not linked any payment card to the account or if there’s insufficient PayPal balance. Additionally, the trojan’s malicious Accessibility service keeps waiting in the background and activates as soon as the PayPal app is booted. This means that it can automatically transfer money from the victim’s account multiple times. WeLiveSecurity has reported this malicious technique to PayPal, along with the account used by the attacker to receive stolen funds.
There’s also an additional method by which the trojan can steal user’s credentials. It uses a screen overlay that draws over apps like Google Play, Skype, WhatsApp, and others that ask users for their payment information. When users enter their credit card details, the overlay attempts to steal the information. Do note that an invalid input is also accepted by the overlay and it disappears. However, there’s still a chance of user’s data being stolen if they enter the correct details on the first go.
As mentioned earlier, the trojan is not on the Google Play Store and thus, there’s a lesser chance of users falling a victim to it. Unless, of course, you download apps from third-party websites. WeLiveSecurity suggests that one turns off third-party app installs on their phone and download apps only from the official Android app market.
Digit NewsDesk
Digit News Desk writes news stories across a range of topics. Getting you news updates on the latest in the world of tech. View Full Profile