Did you know ‘air-gapped’ PCs and networks exist that never connect to the internet? Here’s why
Air gapped computers explained why critical systems stay permanently offline
What are air gapped networks and how they stop cyberattacks
Air gapping security strategy protects nuclear military and financial infrastructure
In an era where refrigerators tweet and wristwatches stream music, the idea of a computer deliberately cut off from the internet seems archaic. It might even seem counterproductive. We live in a hyper-connected world where being offline usually means something is broken. Yet, in the deepest recesses of global infrastructure, there exists a hidden archipelago of isolated computers. They are designed never to send an email, browse a webpage, or connect to the cloud.
 Survey
SurveyAlso read: DHRUV64 explained: Why India’s first 1.0 GHz, 64-bit indigenous processor matters
What is an air-gapped PC?
This security strategy is known as air-gapping. The term is literal because there must be a physical gap of air between a secure computer and any other unsecured network. There are no Ethernet cables leading to the outside world. Wi-Fi and Bluetooth cards are often physically removed from the hardware at the factory level to prevent accidental bridging.
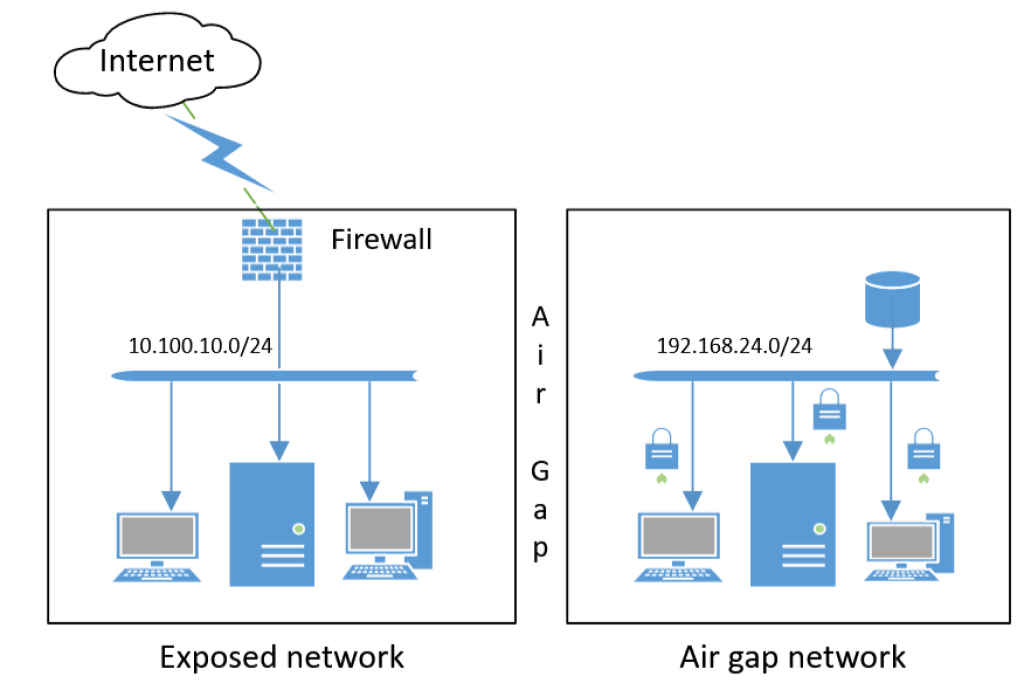
Protecting critical infrastructure
Also read: World’s 1st byte-level AI models: Bolmo 7B and 1B explained, how are they different
Why go to such paranoid lengths in a digital age? Because for certain organizations, the stakes of a cyberattack aren’t just inconvenient. They are catastrophic. Air-gapped systems are the gold standard for protecting critical infrastructure. You find them in the control rooms of nuclear power plants to ensure a remote hacker cannot manipulate reactor core temperatures. They are the backbone of military defense networks housing classified intelligence and weapons systems. They are also used on high-stakes financial trading floors. Intense security is required there to protect proprietary algorithms and prevent massive market manipulation. In these environments, software firewalls are considered insufficient. The philosophy is simple. If a path exists, a sufficiently skilled attacker will eventually find it. By removing the physical pathway entirely, you theoretically remove the threat.
The ‘Sneakernet’ vulnerability
However, this extreme isolation creates a unique paradox. If data cannot travel over a wire, it must be carried by a human. This necessity introduces the weakness of the air gap known as the sneakernet. Updates, patches, or new commands must be transferred manually via physical media like USB drives or external hard disks. This human bridge across the digital divide is where vulnerability creeps back in. The most famous example of this is the Stuxnet worm discovered in 2010. Stuxnet was a sophisticated cyberweapon designed to sabotage Iran’s nuclear program. It successfully crossed the air gap into the Natanz uranium enrichment facility not via the internet. It likely entered through an infected USB stick plugged in by an unwitting employee or contractor.
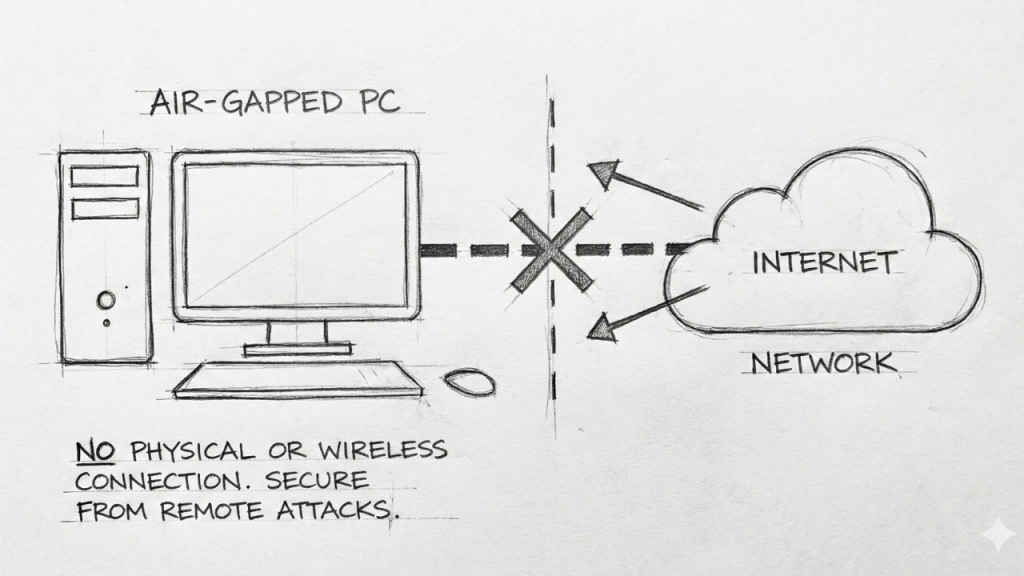
The existence of air-gapped networks proves that the ultimate form of modern cybersecurity is actually a return to pre-internet physical isolation. It is a powerful defense. However, it serves as a stark reminder that while you can disconnect a machine from the web, you can never fully disconnect it from human error.
Also read: AI agents to India’s internet boom: Cloudflare highlights 5 epic things of 2025
Vyom Ramani
A journalist with a soft spot for tech, games, and things that go beep. While waiting for a delayed metro or rebooting his brain, you’ll find him solving Rubik’s Cubes, bingeing F1, or hunting for the next great snack. View Full Profile