‘Avast Ye! Hack’rs vs c’rp’rations
The early piracy scene began from the split-up of Bell System, breaking AT&T’s monopoly on the telephone and modem industry in the 80s.
Piracy is ever-pervasive and omnipresent in the ocean of the Internet.
It’s a battle of minds and code, and only time will tell which side will genuinely reign supreme.

Piracy. The word takes its root from the kings of the seven seas, the robbers scouring the waves, plundering and looting from the rich and living a life of criminal adventure. Of course, the modern pirates are a lot less glamorous. They surf the waters of the internet, combing it methodically, to find and crack paid software and redistribute it illegally, available for anyone to download and utilise without spending a dime.
 Survey
SurveyThe early piracy scene began from the split-up of Bell System, breaking AT&T’s monopoly on the telephone and modem industry in the 80s. The infrastructure change that resulted gave many smaller parties access to the inner workings of these systems and the subsequent techniques of breaking them and bypassing them. Circulation of video games burnt onto unmarked floppy disks began in these parties. Over time the parties grew in size and influence, and eventually, they were collectively referred to as the “Warez” (pronounced wares), deriving from the term Soft‘wares’. With the introduction of peer-to-peer (P2P) networks and Torrents, Warez grew in popularity and demand, and the older physical systems of sharing declined slowly. The modern piracy scene runs almost purely on Torrents, and any step to neutralise it is rendered useless due to its decentralised nature.
But that isn’t particularly interesting now, is it? A single click, a bit of waiting and the game of your choice are just there, ready to play; there isn’t a story to tell. So let’s talk about the more fascinating counts of piracy.
Nintendo 3DS:
Nintendo is an interesting company to talk about when viewing from the lens of piracy. It’s a company that solely makes games for its consoles and has produced some of the most notable and historical series of handheld consoles and video game franchises. They have one of the most robust catalogues of awe-inspiring games, making them a very high priority target for cracking both the games they release and the consoles themselves. The security of the 3DS was designed keeping in mind the breach of the Wii. However, it had one major loophole: The 3DS was capable of backward compatibility with DS games.
GateWay, a company involved in cracking games, released chips to break the 3DS entirely two years after its launch. The technique they used was clever: Using the pre-existing hacks available for the DS, they took control of the DS portion of the 3DS. From there, they overloaded the parent system being the 3DS, with information that was more than the hardware of the 3DS could handle. While in this vulnerable state, the chips would crack the whole system and make it capable of running ROM hacks and other chips without paying for the copies of the game. There were patches by Nintendo and subsequent counterplays by GateWay, who eventually stayed on top of this cat and mouse game. Any competition to GateWay was also crushed by including measures for bricking devices that used said competitor’s cracking techniques, which ended up putting GateWay in a negative light, and people began looking for alternatives. Another issue was the lack of support for HomeBrew, the launcher for games made by solo devs for the 3DS, which bypassed the hardware restrictions created by Nintendo to prevent unauthorised development.
During the release of the new Nintendo 3DS, consisting of minor software and hardware upgrades, a new exploit was discovered, and it involved a poorly programmed game called Cubic Ninja. The newly named Ninjhax utilised a similar technique to exploit the security of the 3DS. Cubic Ninja allowed for user-designed levels, and there was no code to validate the actual size of these levels. So by “creating a level” that was ridiculously large, the system would once again be overloaded and put into a vulnerable state, which would act as the entry point for even stronger hacks. The difference between this and GateWay was that Ninjhax allowed the launching of HomeBrew games. The cracking war would continue to be waged, but these two significant events marked the early days of hacking the 3DS. The entire history of hacking the 3DS up to 2021 can be found in this forum post by user Zoogie.
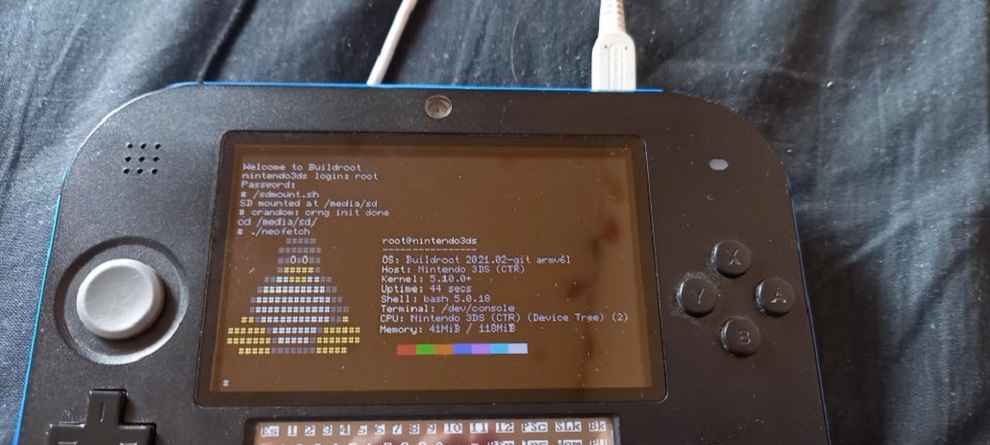
Linux Arch on 3DS
Playstation:
Sony’s PlayStation is iconic as one of the most powerful and accessible consoles in the modern era. The first PlayStation used a region lock to confirm if the disk was made for the specified region and check if it wasn’t a duplicated disk with the contents of an original game. The way to bypass this was crude but simple: by switching an original disk with a fake disk after the region check, the console would think the game had passed the region check, but in reality, the switch had loaded an entirely different game. Mod-chips eventually automated this, which were easily soldered onto the motherboard.
As the chips grew rampant, Sony struck back with a patch. The mod-chips were always active, and they would return information about the region location whenever triggered. So by checking for the region when the system should return nothing, it could detect its presence and invalidate the game being played. There was an additional 16-bit key that was on the ROM itself and added as a backup piracy check. However, both measures were soon overcome, which brings us to Spiro, Year of the Dragon.
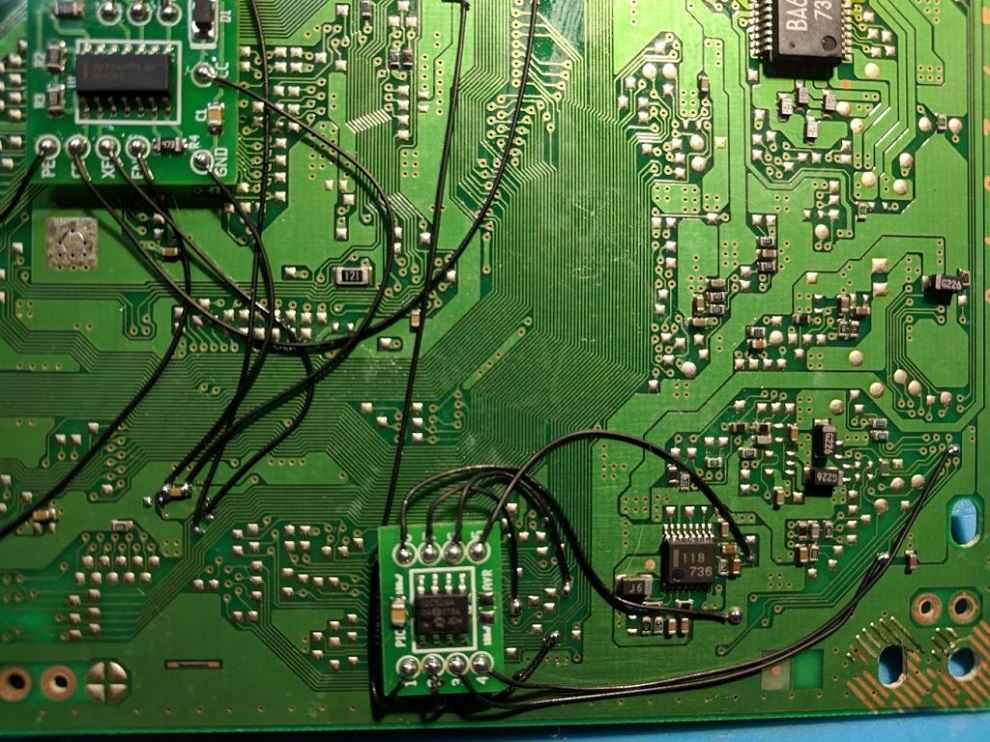
Mod Chip on a PS motherboard
Every other game with the new set of protections would instantly fail if the console caught the run disk as a fake copy. The crackers would simply bypass that, and once the game would boot and the first few minutes would play, they would be satisfied that crack was successful. However, Insomniac Games had a clever checksum system to recognise if the copy of the game was a pirated one. It would be quiet about it till a little further down in the game, something the cracking community didn’t check. At that point, one of the characters in the game would inform the player that the game was a pirated copy and they could continue playing it, but they might experience some strange issues. The player would lose gems, their egg collection progress, and the game would randomly crash and save data would be lost. The goal was to make the experience of trying to play this incorrectly cracked copy as infuriating to play as possible. And that wasn’t even the most annoying part in all this. The hidden protection system had checked, checks for those checks, red herrings, and obfuscated code, making breaking the system all that more difficult. The leading cracking group at the time, ParaDox, took an extra couple of months to bypass all the hidden checks and protection and even thanked the developers and programmers on the game for giving them such a challenging task.
PlayStation 3:
Sony was no stranger to piracy and modding, and with the release of the PS3, they were determined to make sure they created the ultimate “unhackable” console. The PS3 and the Xbox 360 had a hypervisor set up, which acted as an all-mighty gatekeeper, protecting the console from hacks. Hackers shredded the Xbox protection pretty early on with hardware attacks, but the PS3 was safe for around three years. It was considered a successful launch of a console, probably the greatest in video game console history. But it was about enough time for some expert hackers. George Hotz (aka Geohot) was a renowned security researcher who decided to dive headfirst into breaking the PS3.
The PS3 supported a framework called OtherOS, which treats the PS3 like a regular machine capable of running user-installed software, including Linux distributions. The most popular of these was Yellow Dog Linux, and Geohot theorised that this could be the entry point for the hack. Sony instantly went into a state of panic, and they believed that this compromised their hypervisor and instantly nuked the OtherOs functionality with further updates. This was a massive blow to the PS3 as OtherOs was one of the major selling points for the console.
Accessory to jailbreak PS3
Furthermore, Sony hadn’t adequately explained why they removed OtherOs from the PS3 since there was no actual hack available yet. It resulted in a class-action lawsuit being launched against Sony for being “unfair and deceptive" and a "breach of good faith". Sony was willing to separate from millions of dollars to patch out the last potential source of a breach.
However, this was the only further incentive for people to take hacking the PS3 much more seriously. A PS Jailbreak device was released into the black market and sold a few months later, running cracked and unsigned code on the device. The exploit was based on Sony’s same principle to set the PS3 into a factory service mode. Subsequently, the hack would later even allow rolling back versions, allowing users to access OtherOs. The price of the PS Jailbreak device was incredibly high for the service is provided. Still, others in the community eventually reverse-engineered the hacking process is performed and made it open source for anyone to execute on their PS3 for free.
Conclusion:
Piracy is ever-pervasive and omnipresent in the ocean of the Internet. The Warez scene will forever remain active for many reasons, ranging from the accessibility of games in regions to not being able to shell out the exorbitant amounts charged for modern triple-A titles. It’s a battle of minds and code, and only time will tell which side will genuinely reign supreme.