How to bypass system administrators and access blocked sites from office
There are virtual gatekeepers sitting on your network traffic right now. But system administrators are not as bulletproof as they might seem!

Remember when you quickly went on to Facebook while on a coffee break at work? How about that time you opened up a Torrent site in the college computer lab? You thought you got away with it and no one noticed? You’re probably wrong, because System Administrators or sys-admins (or sss-admins – because people compare them to snakes) see everything! They’re not too liked because of how rigid they can be.
 Survey
SurveyRemember, though, don’t hate the person, hate the position, because he or she is just doing their job. That disclaimer aside, it’s time to learn how to stick it to them! Remember, though there can be serious consequences for such actions, and losing your job, or even prosecution and jailtime might be on the cards, depending on where you work. Plus, if you happen to be an actual sys-admin, this article might help you learn how people are bypassing your restrictions. Now that we’ve saved our collective backsides from lawsuits, on with the article!
The restrictions
Sys-admins are a bunch of tools. No, that came out wrong, what we meant was that they use a bunch of tools. First step in bypassing the tools is leaning about them yourself:
- Network firewalls – These block incoming and outgoing access to whatever the sss-admin wants to block – websites and IP addresses.
- Installation access – If you’re unable to install or upgrade things on your system this is because of restrictions on installations.
- Process list – You may be barred from being able to view or change the current running processes on your system.
- Blocked ports – You may be barred from accessing certain TCP/IP ports which some services might require to be open in order to run.
- There might be a few other restrictions in place as well, but they will be similar to the ones we’ve mentioned here, and you can bypass most with the knowledge you get from this article.
Embrace your snakehood
While most sys-admins try and lock you out of the important settings of your computer, here’s how you can lock them out instead:
If you’re on Windows, just restart your computer. When you get to the ‘Starting Windows’ screen, hold down the power button on your PC/Laptop to shut it down again. Start it again and you should be at the Windows Error Recovery screen. Choose Launch Startup Repair and let the repair go through (if the System Restore dialog pops up, hit [Cancel]). When you get to the screen that says Startup repair cannot repair this computer automatically, click on ‘Show problem details’ and scroll to the bottom and click on the last link, which is when Notepad should pop up. Go to File > Open and open the local disk (C:/ in almost all cases).
Go to Windows/System32.
The next part is extremely important and doing it wrong might break the machine, so follow it carefully. You should be still within the Open dialog box. Change Files of type to All files. In the directory list above, scroll down and find cmd.exe and make a copy of that in the same folder (cmd-copy). Next, find sethc and rename it to sethc1, and then rename your cmd-copy to sethc. Close the Open dialog, then notepad and hit Finish to restart your machine.
Once you are back on the Windows login screen, press [Shift] five times to open up the command prompt. The next step is to find out the local administrator for your PC. Type net localgroup Administrators and typically look for an administrator name that does not have the domain related (school/workplace) name in front of it. This will probably be a random string of characters, as that is what most sys-admins tend to put up, to deter people trying to break in. Once you have identified such an account, time to change its password. Type net user <ACCOUNT NAME HERE> * hit [Enter] and type the new password twice (Don’t worry if it doesn’t show your keystrokes, it does still register them). One last thing to check before you can log into this account is if it has been kept active by the sys-admins. Type net user <ACCOUNT NAME HERE> /active:yes. This should activate the account, had it been inactive, and now you can log in to the administrator account with the new password. It’s a good idea to replace the new sethc file with the original one once you are done.
Network firewalls
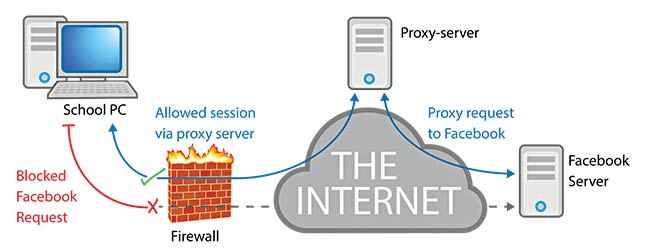
One of the most common ways to get around a firewall is to use a proxy website. Of course this is common, so any decent sys-admin will have already blocked all commonly known proxies. Get Firefox installed (even if you have to get it via the sys-admin themselves). Start Firefox and go to Tools > Options > Connection Settings. You can find a list of available proxy IP addresses online as well.
A more reliable option would be to use UltraSurf or JonDo. Both use the self-invented GIFT system which is a high-encryption node-proxy anti-jamming system that allegedly has higher security standards than even financial transactions online. Both UltraSurf and JonDo are simple EXE files that connect automatically to a proxy server. They are portable software and can be run from a USB drive. Some systems have USB access restricted though.
You can also use remote access if you have a home PC on an unrestricted connection you can use that as your private proxy server to browse using its connection. Just go to Start > Accessories > Remote Desktop Connection. If your home computer has a static IP address, put that in (if it does not, then sign it up with dyndns.org to associate a name to your computer). Once connected, you can use it like a virtual machine.
Using your phone’s mobile data hotspot is another way of bypassing all internet restrictions. You could also use a VPN service to be able to browse freely, over an encrypted connection.
A rough representation of how a proxy server can help you bypass a network level filter
Installation Access
If you are mainly reliant on a school or university computer for projects, research and more work, it can get particularly irritating when you want to use a free and legal tool that is essential for your project and you simply don’t have access to do it. Even on a work PC, getting the admin department to install something for you each time you need it can be a real pain. Besides, what harm can VLC really do to a machine?
One of the simplest ways to get around this is to get portable versions of the applications that you need on a USB drive and run them on your target machine. Contrary to what you expect, portable versions are available for a large number of applications. Head over to portableapps for a full list that contains all the categories and options that you will need.
Another method involves getting the installer file to extract into a folder.What this method does is, it simply gets the files that the installer would normally place in the installation folder, into another folder of your choice by making the installer behave as an archive. Keep in mind that this is trial and error method and may not work with all applications. Once you have the installer files with you, you need to download an application called the “Universal Extractor”.
Once you have the application, run it, and in the window that opens up, choose the correct option to select the installer to be extracted. It also lets you select the target folder, which is the same folder as the installer by default. Once you have done this, you will be prompted to select the extraction method. If you are not sure about the method here, try each choice once until you get the extracted files in that folder. Now you can simply copy these files onto a USB and run them on a computer of your choice.
Unblock ports
For this one, you will absolutely need admin access, so refer to the earlier part of this article if you skipped it. Once you’re done with that, or if you already have admin rights, there are essentially four ways in which an admin could have blocked your USB ports, and we are quickly going to take all four of them down!
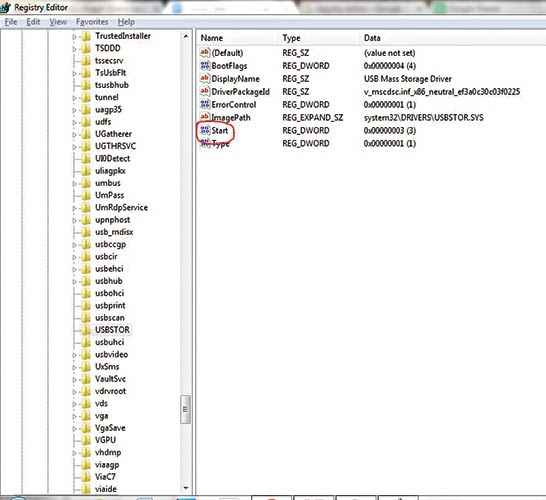
Method 1 – go to Start > Run and type regedit and hit [Enter]. Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\USBSTOR and on the right pane, click on Start and change the value to 3, then hit OK.
Method 2 – Just check the device manager, as ports can be disabled from here as well. Right click on a selected port and click on Enable
Method 3 – If your sys-admin has gone one step further and uninstalled the USB drivers completely, simply plugging your USB device back into the machine should start a search for the right drivers and their subsequent installation.
Method 4 – Get a third party tool to enable USB ports. Such tools are usually one-click solutions to enable/disable ports, and you can find quite a few good ones online.
The default value on an untampered system should be 3
Access the taskmanager
Thanks to the super efficient operating system that Windows has been, and the tendency of school or work systems to be ‘extremely generous’ with configuratioins (that’s sarcasm), sometimes the only option one is left with is opening up the task manager and killing unnecessary processes. Sadly sss-admins have been known to block this as well. You need one all powerful tool to get beyond this unbreachable wall, and that tool is…(cue drumroll)….Microsoft Word!!!
No, we’re not kidding, really. There is a loophole in Microsoft’s Office software for creating documents that has associated a ‘Tasks’ property to it, that conveniently returns a list of all the processes running on the computer. There are a number of things you can do with this loophole which involve running some scripts using the command prompt, that lets you do all sorts of things like getting a list of processes, closing a process or even maximising it. Check out the exact process here.
Caution!
Again, we want to reiterate that most of what we’ve shown you here can actually land you in serious trouble. Losing a job might just turn out to be the smallest punishment for you. Before you run amuck on your work or college network using these hacks, please think things true carefully. Maybe, instead of being malicious, it would be best to approach your system admin and work on this together as a project to test whether these hacks work. She might just turn out to be grateful for showing her these tricks, and allow you to bend or even break some rules in the interest of white hat hacking and helping secure the network! Then again, maybe not. Either way, be warned!
This article was first published in September 2016 issue of Digit magazine. To read Digit's articles first, subscribe here or download the Digit e-magazine app for Android and iOS. You could also buy Digit's previous issues here.