‘Ghost Telephonist’ attack allows hackers to hijack 4G enabled smartphones and pretend to own them
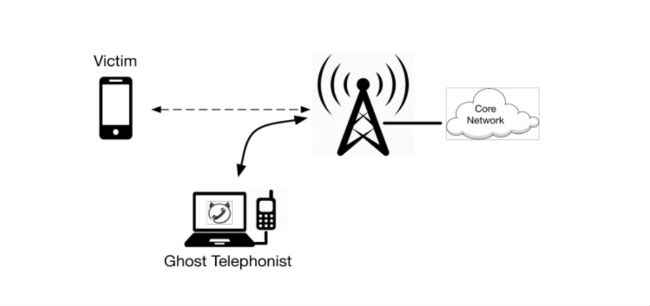
A Ghost Telephonist attack usually occurs when your phone is trying to switch from 4G to 2G in case of low connectivity. Hackers can exploit a security flaw during this process and gain access to your phone number within 60 second, allowing them to pretend to be you.

How many services is your mobile number linked to right now? How many contacts do you have on your phone? Do you receive OTPs on your mobile numbers? Now imagine if someone used your own number against you. Imagine if your bank accounts are emptied because the authentication code that was sent to your mobile number was also accessible to hackers. Think about what could happen if your contacts received messages from you asking for money, without your knowledge.
 Survey
SurveyAll this and more is possible with something called as the ‘Ghost Telephonist attack’. Hackers can gain access to your mobile numbers when your 4G phone switches from a LTE network to an older 2G network. A smartphone usually switches from 4G to 2G multiple times in a day, without users paying much attention to the process. Usually, a phone is required to send authentication codes when connecting to any network to prove its identity as the device that houses your number. However, when a phone switches from a 4G LTE network to a lower 2G network, this authentication is not required. This gives hackers a window to get the victim’s phone number and make calls, send messages, gain access to online accounts and more through their own handsets. The Ghost Telephonist attack can be executed in a span of 60 seconds.
The attack was first discovered and named by a Chinese internet security firm, 360 Technology, which makes anti-virus software for PCs and mobile phones. A team from the company presented details on Ghost Telephonist at the on-going Black Hat security conference in Las Vegas. At the event, the security research team named Unicorn, presented a scenario where one could reset a Facebook password by using a stolen mobile number. Since Facebook sends authentication texts to a user’s mobile, hackers can intercept the text on their clone of the user’s number, thereby compromising the account in question.
The Unicorn team is presenting its findings to various telecom providers so that they fix their authentication process while networks switch from 4G to 2G. Currently, the only way to block Ghost Telephonist is to switch your phone to Airplane mode.