Twitter breached, attackers stole 250,000 user data
Iinvestigation revealed that attackers were able to access a subset of user data, including usernames, email addresses, session tokens, and encrypted/salted passwords, belonging to approximately 250,000 users
Attackers may have gained access to 250,000 accounts on Twitter, the microblogging site said. It’s time to change your password…again.
 Survey
SurveyThe site’s security team identified multiple access attempts by unauthorized individuals to access user data this week, the Bob Lord, director of information security, wrote on the Twitter blog on Friday afternoon. The company also uncovered “one live attack” and shut it down while it was still in progress moments later, Lord said.
Further investigation revealed that attackers were able to access a subset of user data, including usernames, email addresses, session tokens, and encrypted/salted passwords, belonging to approximately 250,000 users, Twitter admitted in the post. Lord did not provide any additional information about the security breach, nor did he say whether any of the exposed accounts had been illegally accessed.
“As a precautionary security measure, we have reset passwords and revoked session tokens for these accounts,” Lord wrote.
Paul Ducklin over at Sophos explains what attackers can do with stolen session token on the NakedSecurity blog.
Reset Passwords!
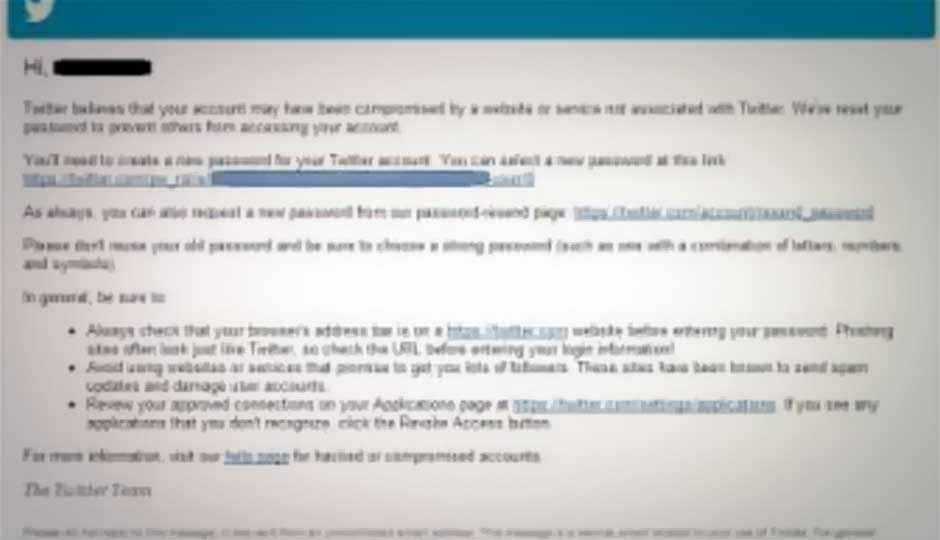
After resetting the exposed passwords, Twitter notified affected users by email to create a new password. The email recommended users select a strong password—at least 10 characters and not reused on any other site or accounts—to protect themselves. Of course, a password longer than 10 characters is also better.
If the user had a weak password, the fact that Twitter had salted and encrypted the passwords would not be much help, as attackers can use various password cracking tools to figure out what the original password string was. And if users had used the same password for other sites online, that’s the keys to the user’s identity kingdom, right there.
The notification email from Twitter is cryptic, to say the least. It doesn’t mention the attack at all, nor does it link to the actual blog post. It just informs the user the password may have been compromised and offers the user a link to click on to reset the password. There are a other links to other parts of the site in the email.
The letter “had all the hallmarks of a phishing e-mail,” Twitter user Simon Phipps wrote. “Users should NOT be trained to accept this,” he added.
We at SecurityWatch have said it before and we will say it again: Don’t click on links in emails. Anyone can mock up a note like this and send it out to random users. As Phipps noted in a different tweet, it would be “hard to tell straight away.” There were reports on Twitter that a spam campaign may already be in progress.
If you receive an email asking you to reset your Twitter password, just take a second to manually go to Twitter’s site and click on the “Forgot password” link. If you have to click on a link in an email, at least click on a link in the email you requested.
Whodunnit? Who Knows?
Lord did not speculate as to who may have been behind the attacks.
“This attack was not the work of amateurs, and we do not believe it was an isolated incident. The attackers were extremely sophisticated, and we believe other companies and organizations have also been recently similarly attacked,” Lord wrote.
However, Lord’s post mentioned the attacks against the New York Times from China this week and the recent advisory from the Department of Homeland Security recommending users disable Java in their browsers. While Twitter is reported to use Java in its infrastructure, there don’t appear to be any Java applets on the site itself, so the recommendation to disable Java in the browser is puzzling in this context.
Federal law enforcement and government officials are investigating the incident, Twitter said.