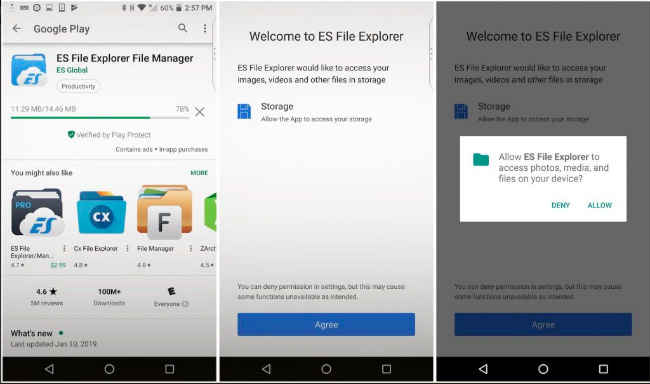
ES File Explorer security flaw can aid hackers to leak data on Android devices: Researcher
The ES File Explorer app is claimed to have a web server running in the background which opens up the Android device on which the app is installed to attacks, including data theft.
Highlights:
 Survey
Survey- Researcher finds security flaw in ES File Explorer app on Play Store
- It can allow attacker to steal data, like photos and videos from the device
- The chances of exploitation with this are less
French security researcher Baptiste Robert, who is popularly known as Elliot Alderson, has found a vulnerability in ES File Explorer app, which he claims can aid attackers in stealing the data on any Android device on which it is installed. ES File Explorer is an app with more than 500 million downloads and people use it to browse through files like documents, photos and videos on a phone of tablet powered by Android OS.
While disclosing his findings in a number of tweets, Alderson says that the app has a running web server on the device, and that server make the entire device vulnerable to data theft attack. Arguably, some have suggested that the server is used to stream video to other apps using the HTTP protocol. TechCrunch claims that prior to tweeting, he showed the publication how an exposed port could be used to silently exfiltrate data from the device.
The news platform says that the researcher wrote a simple script and demonstrated that he could pull pictures, videos and app names — or even grab a file from the memory card — from another device on the same network. It was also demonstrated that the script can even allow an attacker to remotely launch an app on the victim’s device. TechCrunch claims to have tested the script and found the claims to be legit.
The report says that there are little chances of exploitation because anyone on the internet cannot execute the attack. In order to compromise the device, the phone and the attacker has to be connected to the same network (or WiFi). But there is a possibility that any malicious app on any device on the network that knows how to exploit the vulnerability can pull the data from a device running ES File Explorer and send it along to another server for as long as it has network permissions.
Related Read:
Patanjali's 'Kimbho' app busted
Image Courtesy: TechCrunch
Digit NewsDesk
Digit News Desk writes news stories across a range of topics. Getting you news updates on the latest in the world of tech. View Full Profile