The need of cyber-security
Millions of accounts hacked! User data leaked! Massive data breach! The need for cyber-security has never been greater than now

It’s probably safe to say that our days begin and end with us peering at some digital screen or another. We wake up to alarms on our phone, check our emails on it, order groceries, services and various other items on them, pay for these utilities online, and capture and store pictures and videos on them, more often of a personal nature than not. We’ve practically given away huge chunks of our lives on the cloud, and it’s very rare for anyone to stop and think of the possibility of our data falling into the wrong hands.
 Survey
SurveyBut it’s happening here and now, in front of our very own eyes. You’d have to be living under a rock if you don’t know about the massive data dumps that have been posted on the internet recently. Large amounts of confidential data, not limited to names and physical addresses, but also sensitive information such as credit card details and account passwords have been compromised, and have generally stemmed from a security breach of a large corporation’s servers. And considering our increasing reliance on computer systems and “smart” devices, including smartphones, televisions and other electronic devices that are part of the Internet of Things, we’ve only started providing more ammo to hackers and cyber-terrorists, looking to create havoc and disrupt our routine.
Such incidents only further emphasize the need to safeguard our data and proceed with caution when giving away personal details on the internet. For those who still are unable to fathom the gravity of the situation and the threat these cyber-criminals pose to our life, we’ll just take a look at some incidents of mass hacking that have had severe consequences for all parties involved.
If we look at the LinkedIn hack, back in 2012, passwords for nearly 6.5 million user accounts were stolen by Russian cyber-criminals, and many were unable to log into their accounts following the theft. A LinkedIn hack might not seem like such a big deal for those who don’t use the website regularly, but the theft in 2012 turned out to be worse than anyone anticipated. In May 2016, an additional 100 million email addresses and hashed passwords were leaked from the same 2012 breach.
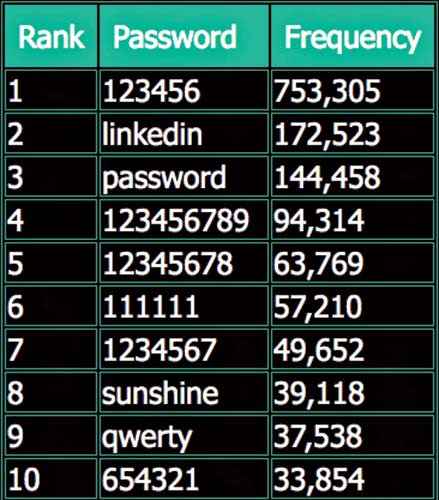
And soon after the leak, dozens of celebrity Twitter accounts were hacked, including that of Mark Zuckerberg. All signs pointed to the fact that Zuckerberg used the same LinkedIn password for his Twitter account, which is a pretty common mistake. Another problem that was highlighted after analysing the data dump was the lack of password etiquette, despite people being constantly told to keep different passwords for different accounts. LeakedSource published a table about the most commonly used passwords on LinkedIn and it’s the stuff made of cyber-security nightmares. The most commonly used password is “123456”, second most common password was “linkedin” and then came “password”, at the third spot. It must be noted that the hack occurred in the first place because LinkedIn stored the passwords in SHA1 with no salting, which makes them extremely easy to crack.
The LinkedIn hack’s most common passwords
Apple iCloud
There’s also the iCloud break-in of September 2014. Hackers stole a collection of almost 500 private pictures of various celebrities, mostly women, such as Jennifer Lawrence and Kate Upton from their iCloud accounts. The images were believed to have been obtained via a breach of iCloud but it later turned out that the hackers could have taken advantage of a security issue in the iCloud API which allowed them to make unlimited attempts at guessing the victims’ passwords. In this case, the blame rests with Apple and its security mechanisms. But it also serves as a vital lesson for us to avoid storing compromising and/or personal data on any public server.
Sony
And who could possibly forget the infamous hacks on Sony servers, once in 2011 and another in 2014. While the 2011 attack led to seven million PlayStation Network and Sony Online Entertainment account details being stolen, including but not limited to credit and debit card information, but the 2014 hack reared its ugly head of economic loss. Data included personal information about Sony Pictures employees and their families, e-mails between employees, information about executive salaries at the company, copies of then-unreleased Sony films, and other information. Millions of dollars were lost because of the leaked movies, and the studio was left worse for wear due to the loss in reputation. It might be worth noting that the 2014 attack was instigated by the release of Sony’s “The Interview”, which the hackers were against, because of the fictional depiction of the North Korean president’s assassination. Seeing as how most fingers seemed to point towards North Korean government hackers, this incident could be classified as an act of cyber-terrorism between countries.
The movie that ignited the 2014 Sony hack
Ashley Madison
While most of the data leaked from these dumps is recoverable and might not cause damage to one’s personal life, the fallout from the Ashley Madison dump in July 2015 was another story. Ashley Madison is a website caters to people who are already in relationships but still want to date. Hackers allegedly gained access to millions of the website’s customer information database and posted 10 GB of personal data of users, including their names and email addresses. Since the website didn’t ask for email verification for the profile to be created, many fake profiles were created. And since the company required the owner of the email account to pay money to delete the profile, many people with fake profiles or misunderstood names did not bother getting their accounts shut. All in all, many people ended up having their personal details exposed, when they had not intended for the same to happen.
LastPass
In another hack with slightly less devastating consequences, LastPass email addresses and encrypted master passwords were compromised in a breach in June 2015. Many password managers, such as LastPass, were created to address the issue that passwords are a notoriously poor form of security. They function by requiring you to remember one strong master password, that would be used to access the manager’s encrypted vault. It would be this vault that would allow you to generate unique and tougher passwords for your other accounts and store them here for future use. Since people tend to use weak, easy-to-remember passwords, re-use passwords across a multitude of accounts, and forget to change their passwords often enough, this solution worked brilliantly for all parties involved. Unfortunately, this massive breach only proved that even the strongest of ideas to manage password securities can fail.
But all these thefts were on a much larger scale, and more because of negligence on the part of the bigger corporation involved. Billions of internet users are the risk of having personal data stolen right from their laptops because of hackers employing malicious software containing viruses, bots and malware. And the sheer number of people falling prey to these will astound you.
Ransomware
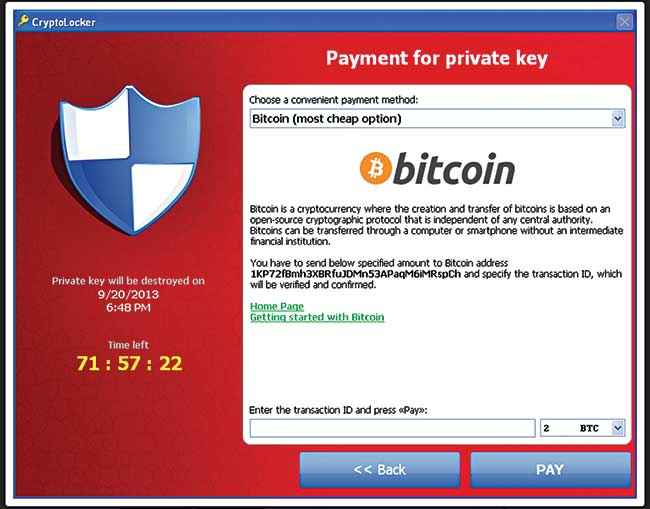
The most current and popular form of virus is a Trojan Horse ransomware. Targeted towards Windows users and propagated through emails, this virus will encrypt certain files on the hard drive and any mounted storage connected to it with RSA public key cryptography. The original ransomware on the market was CryptoLocker, and the hackers would demand a ransom (hence, the name) in exchange for the decryption key. In June 2014, Operation Tovar took down Evgeniy Bogachev, the leader of the gang of hackers behind CryptoLocker, but many knockoffs are still running around in the market, though the affected user base is a much smaller one. CryptoLocker managed to affect around 500,000 users in its 100 days, and the hackers made off with upwards of $30 million with this heist.
The screen on a device affected by CryptoLocker
Keyloggers and Viruses
Then there are the multitude of viruses and malware that steal passwords and user account details by logging in keyboard strokes whenever the user visits any website. There’s the Gameover ZeuS trojan, which steals one’s login details on popular Web sites that involve monetary transactions. It works by detecting a login page, then proceeds to inject a malicious code into the page, keystroke logging the computer user’s details. Zeus was been created to steal private data from the infected systems, it’s still customisable to gather banking details in specific countries and by using various methods.
But the worst of viruses, which is the first example of the potential of cyber-terrorism, is the Stuxnet computer worm, believed to have been created to sabotage Iran’s nuclear program. The virus is typically introduced to the target environment via an infected USB flash drive, which then introduces the infected root-kit into the system, modifying the codes and giving unexpected commands to the computer while returning a loop of normal operations system values feedback to the users. The aim of the worm was to fake industrial process control sensor signals so that the infected system does not shut down due to detected abnormal behaviour.
While most attacks have been limited to computing systems like servers, desktops and laptops, hackers now focus on the IoT ecosystem and all its connected components. Large networks of IoT devices—like CCTV surveillance cameras, smart TVs, and home automation systems are prone to hacking, and the modern age thief will make use of these to carry out coordinated attacks against individuals and corporations. So unless we beef up our arsenal against these goons, they’ll move on to stealing biometric data and personal information that can be used to impersonate fully functioning individuals.