Origins: Computer viruses
Tracing the evolution of what’s been making your computer sick for the past 30 years
The theory and the firsts
 Survey
SurveyJohn Von Neumann discussed the possibility of a self replicating program back in the 1940’s and published a paper on the same in 1966. The paper explored the idea of a mechanical organism being able to replicate itself and damage machines, much like a living organism. Creeper, often regarded as the first virus, was a test program created by Bob Thomas of BBN. While it did not have any malicious intent, it set the precedent for more such viruses to come. In 1974, the Rabbit virus was developed and released. It made multiple copies of itself on any machine it reached and significantly slowed down system performance. The first reported Trojan, ANIMAL, was created in 1975 by John Walker. The first PC virus Brain began infecting 5.2” floppy disks in 1986. Although it had no malicious intent, it was the first stealth virus placed on the boot sector of floppy disks.
The Internet unleashed
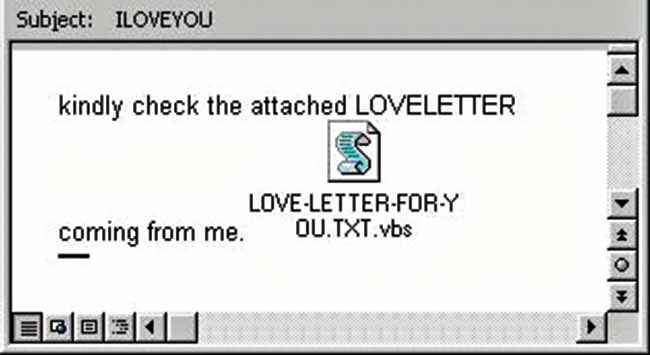
With the arrival of high speed internet and communication network, malicious software no longer relied on floppy disks or internal networks in organisations. It found a new favorite medium – email. Two of the most effective viruses to do this were the Melissa virus 1999 and the ILOVEYOU virus a year later. The Melissa virus took advantage of Visual Basic for Applications, that was built into Microsoft Word to create a word document which, when opened, immediately sent itself to the first 50 people on the opener’s contact list. The ILOVEYOU virus was more human activated as it made no attempt to disguise its executable nature in the form of a .vbs file. And since the person received the message from someone on their contact list, with this name they were highly likely to open it. This virus has gone on to become one of the first documented examples of social engineering.
Worms armageddon
A worm is a computer program whose sole purpose is to replicate and occupy system resources as well as network bandwidth. In 2001, the Code Red worm made headlines by exploiting a flaw in the Microsoft Internet Information Server to spread globally in a few hours. The worm was instructed to replicate itself only for the first 20 days of the month, block web pages on an infected server with the message “Hacked by Chinese” and then, on a certain date, launch a Distributed Denial of Service attack on the White House website.
Recent threats
The kind of viruses that worked earlier don’t work nowadays. We’ve gotten better when it comes to securing our gadgets with tools like antiviruses and firewalls. But malicious code has just shifted its focus towards exploiting flaws in systems and is still causing damage. Take the example of Heartbleed, a vulnerability in the widely used open source cryptographic library Open SSL. It could be used to obtain confidential information by just sending a message of shorter length than declared. Even Android’s Stagefright is more of a bug more than a virus, but it has to be triggered by a specific MMS message (that requires no action from the end user) and grants the attacker complete access to the phone, which might include instantly crashing it as well.
Future of viruses
Malicious code which used to be nothing more than cyber vandalism has now evolved to full fledged cyber crime. And in this connected age, it might be possible to lose access to your devices and information due to the same technology that has enabled their existence. Malware targeting smartphones are emerging now, and soon it will be shifting towards Point of Sale terminals and the Internet of Things. A good example of current capabilities is the Moker remote access trojan. It’s hard to find and remove and bypasses almost all known security measures. The only way forward right now is to change faster than the threats are evolving.
This article was first published in October 2016 issue of Digit magazine. To read Digit's articles first, subscribe here or download the Digit e-magazine app for Android and iOS. You could also buy Digit's previous issues here.