Microsoft servers attacked: The zero-day exploit explained
Hackers exploited an unknown SharePoint flaw to infiltrate sensitive networks before Microsoft could respond.
A zero-day exploit gave attackers undetected access to critical systems across government, education, and telecom sectors.
Microsoft’s SharePoint servers were breached using credential-free code execution, exposing global infrastructure to silent threats.

Zero-day exploits are the ghosts in the machine, silent, invisible, and devastating when they finally make themselves known. Last week, Microsoft confirmed one of the most serious intrusions in recent memory: a zero-day vulnerability in its SharePoint Server platform that enabled attackers to breach critical infrastructure around the world. The fallout has affected government agencies, educational institutions, and private enterprises exposing a dangerous truth: even the most fortified digital environments remain vulnerable.
 Survey
SurveyAlso read: Hackers target Microsoft SharePoint again with critical zero-days, over 85 servers hit
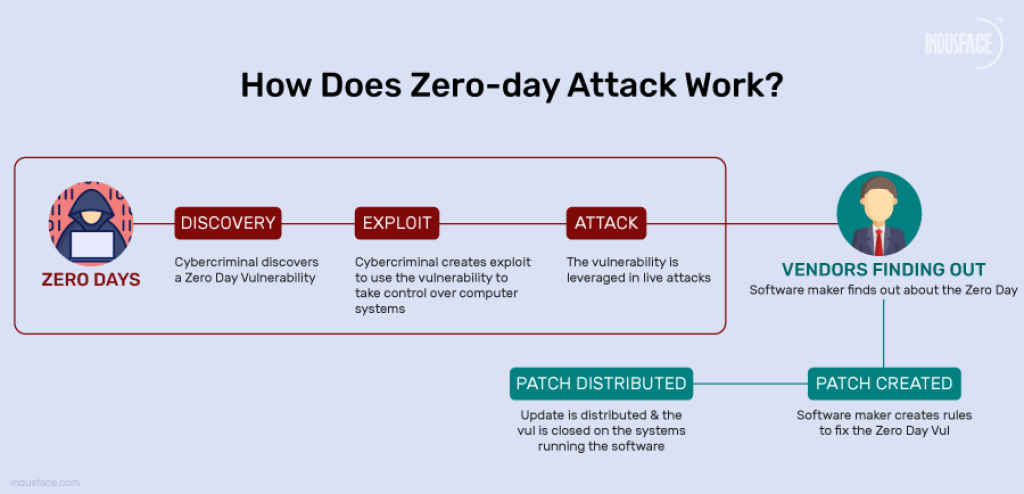
What is a zero-day exploit
A zero-day exploit is a vulnerability in software that is unknown to the software vendor and has “zero days” of warning before it’s discovered and used maliciously. Because there’s no official fix or patch at the time of discovery, attackers can strike with a high chance of success. In this case, the flaw in Microsoft’s SharePoint platform was not just unknown, it was also incredibly powerful. It allowed intruders to remotely execute code without any authentication, essentially handing them the keys to the server.
Once inside, the attackers didn’t just poke around. They planted hidden scripts known as web shells, extracted encryption keys, and quietly created backdoors that allowed persistent access, even after regular system updates.
Not your typical cyberattack
The vulnerability, now catalogued as CVE-2025-53770, was found in on-premises versions of Microsoft SharePoint Server 2016, 2019, and Subscription Edition. It allowed attackers to execute arbitrary code on a server without authentication, making it a powerful entry point into high-value systems. Microsoft disclosed the issue publicly on July 20, but forensic evidence suggests that attackers may have been exploiting it since at least July 18, if not earlier.
Security researchers say this wasn’t just a one-off incident. The exploit is believed to have been used in a coordinated attack campaign targeting U.S. federal and state systems, foreign governments, telecom providers, universities, and energy companies. Victims span across North America, Europe, and parts of Asia. Investigators from the FBI, CISA, and multiple global threat intelligence units are now working to trace the origin and scope of the breach.
Also read: X outage: Hacker group claims cyberattack, Musk hints at coordinated nation-level attack
Unlike ransomware or DDoS attacks that announce their presence loudly, this breach was designed for stealth and persistence. Once inside, attackers reportedly planted web shells, custom scripts disguised to look like normal server files, and exfiltrated sensitive data, including cryptographic keys used to secure internal communications. In some cases, the attackers used legitimate admin tools to avoid detection, essentially living off the land.
What makes this exploit especially dangerous is the nature of SharePoint itself: it’s not just another enterprise tool. It’s the digital glue for many large organizations, housing documents, workflows, and access controls that are core to daily operations. A compromise here isn’t isolated; it often leads to lateral movement across the entire network.
Microsoft responds, but the damage is done
Microsoft has since released emergency patches for the affected versions of SharePoint and strongly urged all organizations to apply them immediately. The company also issued a rare advisory recommending the rotation of machine keys, the cryptographic core that secures SharePoint apps and sessions. They’ve advised system administrators to assume compromise if their servers were publicly accessible prior to patching.
What’s more worrying is that patching alone may not be enough. Security experts stress that organizations need to conduct full incident response checks: examining logs for unauthorized access, scanning for web shells, and ensuring no backdoors remain open. In Microsoft’s own words, “Mitigation requires both patching and forensic investigation.”
At this point, attribution remains unclear. Some cybersecurity researchers point to tactics commonly associated with state-sponsored advanced persistent threat (APT) groups, especially those focused on espionage rather than monetary gain. The attackers made no effort to encrypt systems or demand ransom, suggesting they were after long-term access and intelligence.
However, Microsoft and U.S. federal authorities have yet to officially name any specific actor. For now, they are urging transparency and cross-sector collaboration to share indicators of compromise (IOCs) and build a more complete picture.
A cybersecurity wake-up call
This breach underscores a larger issue that has become impossible to ignore: on-premise infrastructure is increasingly difficult to secure in a cloud-dominated world. While Microsoft 365 users were unaffected by the attack, legacy systems still widely used by public institutions and industries with strict compliance needs, remain exposed to threats that evolve faster than traditional patch cycles.
It’s also a reminder that no software, no matter how critical or widely adopted, is immune to catastrophic vulnerabilities. In an era where digital trust is everything, a single misstep in server security can cascade into a full-blown geopolitical event.
A silent flaw gave attackers an open door to the digital cores of governments and corporations alike. While patches may seal the door shut, the fact remains: the attackers were already inside. The question now isn’t just how they got in. It’s how many more are waiting for the next door to open.
Also read: Microsoft’s Copilot AI can now see your entire desktop screen and here’s why you should be worried
Vyom Ramani
A journalist with a soft spot for tech, games, and things that go beep. While waiting for a delayed metro or rebooting his brain, you’ll find him solving Rubik’s Cubes, bingeing F1, or hunting for the next great snack. View Full Profile