New ransomware attacks users through Android’s Lockscreen UI
The Android.Lockdroid.E trojan uses a sophisticated looking lockscreen to lock up the device and demand money

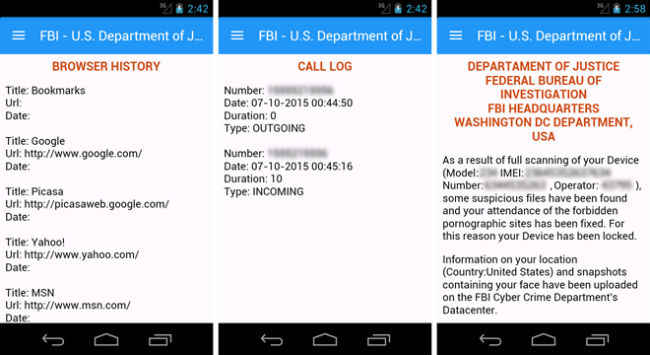
Researchers at software firm Symantec, have discovered a new strain of Android ransomware that imitates the lockscreen user interface to deceive users. The Android.Lockdroid.E ransomware displays a sophisticated lockscreen with genuine looking legal notices to demand ransom for unlocking the device.
 Survey
SurveyThe ransomware can infect devices by disguising itself as a legitimate video app on unofficial app stores. It can also spread from browser hijackers that redirect the search results to the site hosting the malware. However, it does not spread through the Google Play Store. It makes use of Google’s Material Design and an open-source project to create the lockscreen UI. On infecting a device, the malware collects the contacts, call records, messages, and browser history. It then shuts off the user from accessing the device, displaying a fraudulent legal notice. It allows the user to access the “proofs” of the user’s illegal activities through an app drawer on the left side of the screen. “By using the information collected the ransom notice appears personally tailored to the victim. The malware also uses this flaw to display the personal data that it collects through an easy-to-access, official looking menu. These elements help the ransomware intimidate the victim into making the payment,” the press release says.
According to Symantec, Android.Lockdroid.E is allegedly the first ransomware to make use of the Material Design user interface. The developers apparently used an open-source project called “MaterialDrawer” to create part of the interface. Fortunately, the ransomware is not present on the Play Store, and users have been advised to exercise caution while downloading apps from untrusted sources.
A recent study published by University of Cambridge has determined that over 87 percent of Android devices are exposed to at least one critical threat. It has tied the cause to manufacturers not pushing patches and updates on time to the devices. Google’s Nexus devices have fared better in terms of keeping the devices up-to-date. Recently, there have been reports of an annoying trojan that binds itself to popular legitimate apps. The Ghost Push trojan gains root access to the device to download unwanted apps and ads. Some infected apps were also found on the Play Store, but have since been taken down.