WannaCry 101: Everything you need to know about the dangerous ransomware affecting computer systems around the world
As per CERT, very few incidences of the WannaCry ransomware have been reported in India so far. Here is all you need to know about the malware and how to prevent yourself from getting affected.
Over the weekend, you may have come across the word ‘WannaCry’, plastered all over the internet. Afterall, it is one of the biggest malware attacks the world has witnessed in recent times. Yes, infrastructure services, banks, telecom companies, airports and hospitals across 99 countries and 200,000 computer systems have been affected by this massive cyber attack.
 Survey
SurveyAt least two new strains of the malware infection that exploits vulnerabilities in older Windows software such as XP and Windows Server 2003, have been found since the attack was initiated on Friday. As office-goers retired for the weekend, WannaCry hit organisations such as the National Health Services (NHS) in England and Scotland. As per a BBC report, Russia has seen the most number of infected computer systems. Spain’s telecom behemoth Telefonica and utilities firms – Iberdrola and Gas Natural were also hit by WannaCry. In addition, worldwide shipping service FedEx also reported being hit by WannaCry. Governments across the world, including India, are taking steps to educate users about the ransomware. Are you affected? What can you do to prevent it? Here is everything we know so far about the WannaCry ransomware attack
How was WannaCry initiated, and by whom?
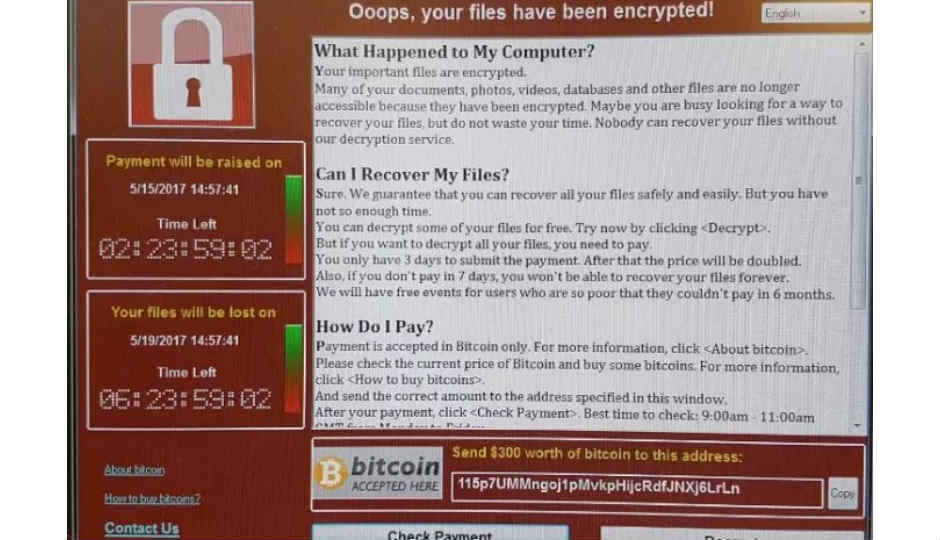
WannaCry is a ransomware that is quick to spread once any computer in an organisation is affected. The WannaCry program then encrypts files on the computer, blocking users from accessing critical information and asking for a payment of $300 to $600 in Bitcoins to unlock files on each affected computer.
Commenting on the attack, Mishi Choudhary, President and Founding Director at SFLC.in said, "This is a flagrant example of a global blackmail facilitated by lax attitude of agencies and organizations on cyber security. In November last year, Sky News and Hacker House had warned about such risks but no heed was paid. Not installing regular software updates is the primary cause for such malware to spread like wildfire. This teaches us how something can wreak havoc without attacking the traditionally designated critical infrastructure like a power grid."
As against most malicious attacks, where people are fooled into clicking on phishing links, WannaCry is a ransomware that replicates itself. It is essentially deployed as a computer worm, which spreads using the computer’s network. This is how WannaCry was able to scale through large organisations in rapid succession.
Below is a tweet showing the ransomware spread across a university computer lab in Italy.
A ransomware spreading in the lab at the university pic.twitter.com/8dROVXXkQv
— 12B (@dodicin) May 12, 2017
Experts believe the malware takes advantage of a vulnerability in Windows PCs that was identified by the United States’ National Security Agency (NSA). Details of an NSA tool named ‘EternalBlue’ were leaked by a hacking group called Shadow Brokers back in April. This tool apparently enabled hackers to add the worm feature to the WannaCry ransomware, giving it the ability to spread across systems.
Although Microsoft had patched the flaw back in March, many users, IT departments in organisations did not apply the update to their systems, making them open to the attack.
Was India hit by WannaCry?
India was indeed one of the countries affected by the WannaCry malware attacks. Although most reports would have you believe that India was one of the worst affected countries, an official statement by the Computer emergency response team (CERT), the national nodal agency responsible for responding to cyber threats, said that “very few reports are reported from our country as well.” CERT issued a nationwide alert on Monday, through a live webcast.
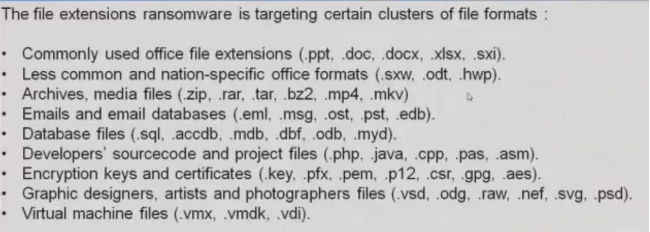
According to CERT, users affected by WannaCry in India are being displayed an English version of the malware’s user manual, which describes how payments can be made, thereby unlocking encrypted files. The response team has also released a list of file extensions that are being affected by WannaCry. These include – .der, .pfx, .key, .xls, .dot, .psd, .moc, .Mp3, and many more popular file formats. Once infected, these files are encrypted with the extension called .WCRY
How can users save themselves from WannaCry?
Thanks to a fortunate accident, MalwareTech registered a URL query which was built into WannaCry, thereby slowing its advance. However, CERT has given out a set of preventive measures which users, organisations can take to avoid the WannaCry malware. For starters, users are advised to patch their Windows systems as mentioned in Microsoft’s Security Bulletin MS17-010. Microsoft has also issued a patch for unsupported versions such as Windows XP, Vista, Server 2003 and Server 2008. The company wrote in a blogpost, “We also know that some of our customers are running versions of Windows that no longer receive mainstream support. That means those customers will not have received the above mentioned Security Update released in March.” The patches can be downloaded from here. Further, organisations and individuals are also advised to take a backup of critical files and store them offline.
More preventive measures are highlighted in this video below
What does Microsoft have to say?
Microsoft President and Chief Legal Officer, Brad Smith, recently condemned NSA’s practices of keeping security loopholes hidden from vendors, only to be stolen by hackers. In a blogpost, Smith wrote, “An equivalent scenario with conventional weapons would be the U.S. military having some of its Tomahawk missiles stolen. And this most recent attack represents a completely unintended but disconcerting link between the two most serious forms of cyber security threats in the world today – nation-state action and organized criminal action.”
He added, “The governments of the world should treat this attack as a wake-up call. They need to take a different approach and adhere in cyberspace to the same rules applied to weapons in the physical world. We need governments to consider the damage to civilians that comes from hoarding these vulnerabilities and the use of these exploits.”
Let us know if you have seen any incidents of the WannaCry ransomware attacks in your organisation or on your personal systems.