How to secure your Linux system
Don’t let the reputation of Linux being more secure than other systems lull you into thinking it can’t be breached. These methods would help keep the system truly secure.

One main advantage that Linux brings to the table (or the desk, if you prefer it that way) is the better security that if offers. Sometimes, the case is such that an antivirus is more ornamentation than utilitarian. But that’s not to say that Linux is an impenetrable fortress within which you can reside safely- a digital cocoon where you needn’t fear any malicious element from entering. Such optimal scenarios are only possible in fantasies-possibly realized with CG made using computers that run on open source.
 Survey
SurveyBut there’s no reason to fret. You are by no means a hapless damsel in distress. There are certain measures you can adopt to further secure your Linux system.
Let’s start with looking at some basic tricks you can use:
Basic tips
Choose Full Disk Encryption
Regardless of the operating system that you use, it’s always advisable to encrypt the entire hard disk. In the event that your laptop is lost or stolen, a login password won’t probably be enough protection. For instance, one can easily boot into Linux from a USB key and read all the data on the system without using the password. By encrypting, it won’t be possible to read anything without using the FDE password.
While encrypting only your home folder and the files contained in it is a possibility, FDE has a significant advantage – you won’t have to worry about breach of temporary files, swap files and other directories where significant files may lie.
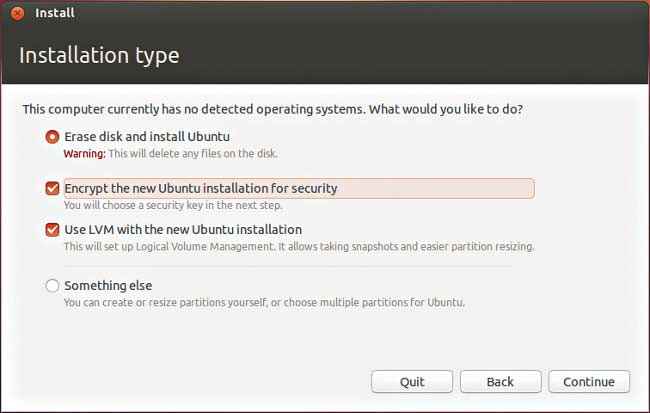
And unless the computer is pre-historic, the slowdown due to encrypting everything on it is barely perceptible. In many Linux distros including Ubuntu and Fedora, full disk encryption can be done during installation itself. You just have to select the “Encrypt the new Ubuntu installation for security” option.
Go all the way, choose it fully!
Keep the software updated
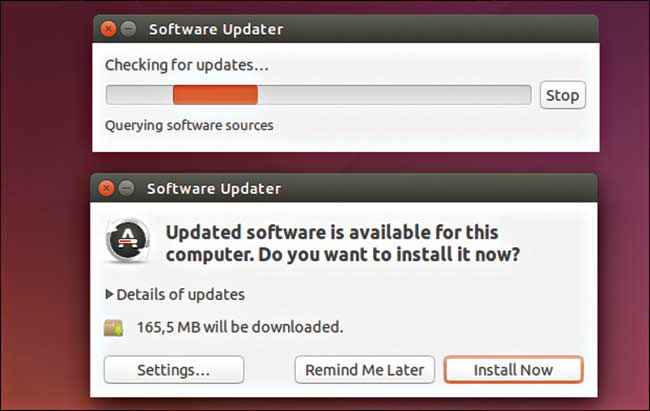
Keeping software up-to-date is so not an exercise in vanity like keeping abreast of the latest trends in fashion without really knowing if they actually suit you or not. Regardless of the OS, you should always keep the OS and other applications-including but not limited to web browsers, PDF readers and video players- updated.
Update, secure.
And it’s easy to perform on most Linux distros. On Ubuntu, for instance, the security updates are automatically installed. To make this happen, just make sure that the “Important security updates” option is turned on by going to System Settings->Software & Updates->Updates
Make use of Linux Firewall
The Linux kernel comes embedded with a Firewall component called ipfire. This offers a pretty effective tool to manage network traffic and also to check different types of cyberattacks. In Ubuntu you will find the application called Uncomplicated Firewall (UFW) which is a frontend program which simplifies setting up iptables.
Stay secure within the wall
UFW would be disabled by default. To turn it on, you can bring up the command prompt and type the following on it:
$ sudoufw enable
A graphical configuration tool like GUFW or UFW Frontends could be a good tool to learn more about ipfire and more relevant – what it can do for you.
Fedora comes with the alternative firewall management toolkit calleFirewallD. It’s enabled by default, so you can chill. A graphical user interface is also available for FirewallD. Called firewall-config, you can install it from the command prompt using:
$ yum install firewall-config
Improve browser security
It’s important to have the browser secured as much as possible since the browser provides the way in for many contemporary cyber attacks. This is true whether you use Google Chrome, Mozilla Firefox, Opera or any other browser for that matter, so no point pointing the finger at any particular one.
However, to improve browser security– and your privacy, multiple free extensions are available. Some of the most effective options include HTTPS-Everywhere, Adblock Plus, NoScript, Ghostery and Disconnect.
Close the chink in the browser!
Use an anti-virus software
Those who are super-confident of the security provisions that Linux naturally brings to the picture(and you’ll be surprised by how many there are) may say that an anti-virus on a Linux system is totally unwanted.
One reason why they say so is that most malware detected on a Linux system will be for Windows. But that doesn’t mean that its not a part of your problem. For instance, what if you pass a corrupted file to someone else.
Don’t be anti anti-virus!
And while it’s a fact that malware on Linux desktops is rare compared to other systems, that still doesn’t mean that they don’t exist. It also doesn’t mean that you are completely immune to attack. After all, rare doesn’t mean zero.
Most secure distros
Tails
One of the more widely recommended distros is Tails, and for good reasons. Tails is actually the short form for The Amnesic Incognito Live System. What makes Tails extremely recommendable is that it’s user-friendly while having significant stress on security. Instead of just focusing on a secure OS, it also ensures that whatever you do on the system also remains secure-at least as much as possible from the get go.
Offers great stability and security
Tails is based on ‘s stable branch, so you can put your heart at ease since it’s known for the great stability and security. Also, Tails runs in a live environment alone which is actually a smart security feature-given how it wipes out completely any trace of use on the system once it’s shut down or restart. Talk about being security conscious from the very beginning!
Just about every need you may encounter is addressed with one software or the other with which Tails come. A customized browser that uses the Tor network is a case in point. Also, in Tails Firefox includes other extensions to make browsing extra-secure with HTTPS Everywhere and NoScript.
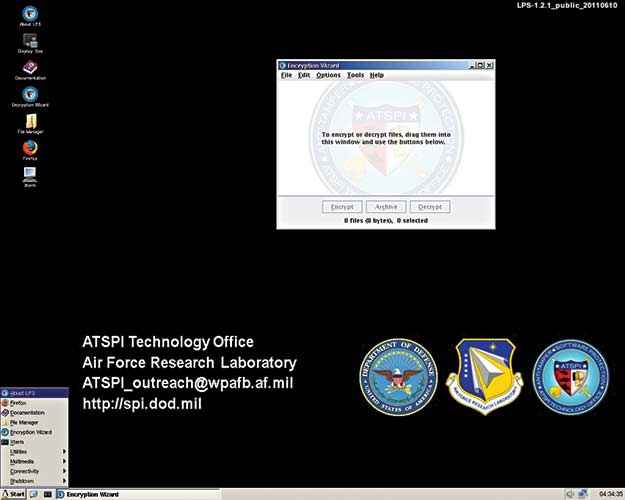
LPS
Lightweight Portable Security or LPS is another feasible option. The distribution, in fact, is maintained by the American Air Force. LPS is also kind of unique for the fact that it has a very minimalistic approach. The hardened code aside, it has a lightweight desktop environment which is akin to Windows XP. The environment includes Firefox and some additional tools. You also get to use what’s called as an “Encryption Wizard” that will help you gain more privacy and security, and which is easy to use.
As with Tails, LPS too runs only in a live environment. And yes, it doesn’t leave traces once you shut down or restart.
Minimal but secure
The common Ubuntu distribution
Just because something is all too common doesn’t necessarily mean that it’s bad. It’s not enough to give you an all-encompassing secure environment like Tails but the OS would be enough to secure your system, as long as your security requirements are regular. You will need to keep the OS updated with available patches using the distribution’s Update manager. Also, you can make things more secure by adding programs like OpenPGP or Tor.
Common, but uncommonly secure!
Make use of Security-Enhanced Linux(SELinux)
There exists a Linux Kernel security module called Security-Enhanced Linux or SELinux. It provides a means by which you can assign security policies for different software, limiting how much data they can access and the functions they can perform.
The users and roles in SELinux needn’t be related to the actual system users and roles. For each current user of process, SELinux will assign a three string context which contains a username, role and domain. Usually, most of the actual users will share the same SELinux username while all access control is managed via the third tag- the domain. You can use the command ‘runcon’ to launch a process into a clearly specified context(user, role and domain). However, SELinux may deny the transition if it hasn’t been approved by policy. Separate measures to protect system integrity (basically the domain type) and data confidentiality is one of the key features of SELinux.
SELinux comes as a part of RHEL Verison 4 and subsequent releases. The supported policy in RHEL4 is not that restrictive, since a key objective is to bring in the maximum ease of use.
Methods for securing the Linux server
Encrypt data communication
It’s common knowledge that any data transmitted over a network can be monitored. However, it’s unfortunately not a common enough practice to encrypt the transmitted data using passwords or keys/certificates. You shouldn’t make the same mistake.
Encrypt data communication whenever it’s needed or possible. You can use ssh, scp, rsync or sftp to transfer files. It’s also possible to mount remote server file system or a home directory with the aid of special sshfs and fuse tools. GnuPG is also something you can use-it allows you to encrypt and sign data and communication and also has a versatile key management system and access modules for all types of public key directories.
Talk safely!
Use only the software that you actually want
We live in an age of choices-especially if you are a netizen. But that doesn’t really mean that you need all those web services installed in the system, does it? If you don’t install unnecessary software, you are by default bringing down the system’s vulnerabilities. You can use an RPM package manager like yum to review the installed software packages on the system. That will give you a good idea of which packages are actually utilized and which are just taking up the space. Remove the latter.
Make a rule of running just one network service per system
It’s always advisable to run different network services on separate servers. This is so that the number of other services which could be compromised can be limited. For instance, if a hacker successfully exploits a software like Apache Flow, then that person gets access to the entire server including other services like e-mail server and MySQL.
Let’s call it the power of one!
Disable root login
It’s never a good idea to login as the root user. Root level commands can be executed, as and when required using sudo. Without sharing root password with other users and admins, sudo enhances the security of the system. It also gives some simple auditing and tracking features as well.
That’s cutting off the root of a problem!
Ensure security of the physical server if you have one
It must be ensured that the Linux server’s physical console access is protected. To this end, configure the BIOS and also disable booting from external devices like DVDs and USB drives. To protect these settings, set BIODS and grub boot loader password. Make sure that all production boxes are locked in Internet Data Centers. Also that everyone should pass through some security measure before they can access the server.
Don’t forget what’s in the brick-and-mortar world!
Delete X Windows
X Windows on a server is not exactly necessary. No reason exists for you to run X Windows on your dedicated mail and Apache web server. X Windows can be disabled and removed to improve server security and performance. Edit/etc/inittab following which set the run level to 3. To remove X Windows system, use the following command:
# yumgroupremove “X Window System”
Turn off IPv6
The Internet Protocol version 6(IPv6) brings in a new internet layer of the TCP/IP protocol suite which not only replaces IPv4 but also provides multiple benefits. There exist no decent tools at present with which you can check a system over network for seeking out IPv6 security issues. IPv6 protocol is set as default by most Linux distros. And bad traffic can be sent by crackers via IPv6 since most admins don’t monitor it. Unless it’s required for the network configuration, either disable IPv6 or set up Linux IPv6 firewall.
Disable unwanted SUID and SGID Binaries
If the SUID/SGID executable faces a security issue or a bug any SEID/SGID enabled file could be misused. Also, any local or remote user could make use of such a file. Finding all such files is then highly recommended. You can use the following command for the same:
- #See all set user id files:
- find/ -perm +4000
- # See all group id files
- find/ -perm +2000
- # Or combine both in a single command
- find / \( -perm -4000 –o –perm -2000 \) –print
- find / -path –prune –o –type f –perm +6000 –ls
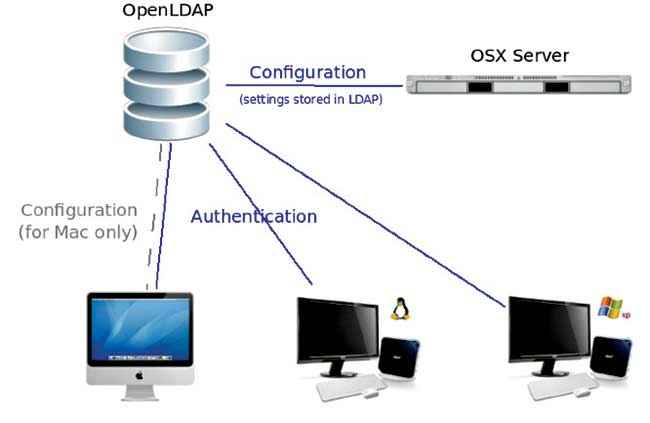
Use a centralized authentication service
Unless there’s a centralized authentication system, user authentication data will become inconsistent. This could lead to out-of-date credentials as well as forgotten accounts that ought to have been deleted. With a centralized authentication service, you can maintain central control over LINUX/ UNIX account and also authentication data. It will also be possible for you to keep authentic data synchronized between multiple servers. Instead of using the NIS service, go for OpenLDAP for clients and servers, if you want to have centralized authentication.
Secure OpenSSH Server
For remote login and file transfer, the SSH protocol is highly effective. But SSH is vulnerable to many type of attacks. So you better make sure that the OpenSSH server is secure.
Install and make use of Intrusion Detection System
A Network intrusion detection system (NIDS) is a useful ally in your fight for better system protection. As the name makes it clear, the NIDS is a system that detects intrusions-more precisely malicious activities like denial of service attacks, port scans and attempts to breach into a computer by observing network traffic.
You will do good to deploy an integrity checking software before the system goes online. If at all possible, you should install AIDE software prior to the system getting connected to a network. For those who don’t know, AIDE is actually a host-based intrusion detection system (HIDS) which could both monitor and analyze a computing system.
In the journey of securing your Linux system, the methods mentioned here will help you go a long way. And those who may wish to breach into your system will always fall short.
This article was first published in October 2016 issue of Digit magazine. To read Digit's articles first, subscribe here or download the Digit e-magazine app for Android and iOS. You could also buy Digit's previous issues here.