Android smartphone OEMs found guilty of skipping critical security patches and lying to consumers about it
Some Android phone makers were found fooling consumers into thinking their phones are updated with the latest security patches. OEMs like Xiaomi, OnePlus, Huawei, LG and Motorola have found to have missed at least 3-4 patches, while MediaTek has also been pulled up for not providing timely security updates to device makers.

Timely software updates are already an issue with Android OEMs and to make matters worse, some of them have been found lying to consumers about security patches. Some Android phone makers have apparently been skipping critical security updates and assuring consumers that they are protected against certain threats when in fact their devices remain vulnerable. Some manufacturers have even gone to the lengths of altering the date of security patches received by devices, while no actual patches were installed on them.
 Survey
SurveyAccording to a report in Wired, researchers Karsten Nohl and Jakob Lell from Security Research Labs (SRL) reverse engineered 1200 smartphones from more than a dozen popular Android OEMs to test their security levels and if they met Google’s requirements. The results of the two year long investigation and testing were shocking as the researchers found a huge “patch-gap” – the difference between the reported security patch level on a smartphone and the actual threats that it is protected against. The “patch-gap” in many cases was found to be appalling and as per the research, some Android OEMs even went to the extent of displaying false security patch updates in a smartphone’s setting without actually installing the said patches. OEMs were found manipulating the date of the security patch shown in settings by modifying ro.build.version.security_patch in build.prop. "We found several vendors that didn’t install a single patch but changed the patch date forward by several months," Nohl told Wired. "That’s deliberate deception, and it's not very common."
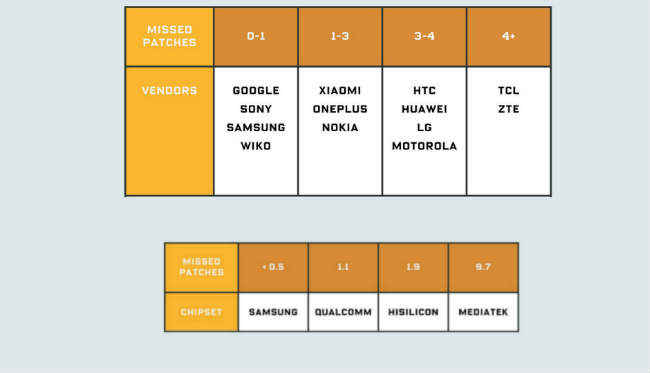
SRL’s testing concluded that apart from Google’s own Pixel and Pixel 2 range of smartphones, even premium smartphone manufacturers like Samsung and Sony were found to have missed some security patches and misrepresented the security level of their smartphones. In a few cases, it was found to be a human error where companies like Samsung and Sony missed a couple of patches, whereas those like Xiaomi, OnePlus, and Nokia were found to be missing at least 1-3 patches. Brands like HTC, Huawei, LG and Motorola were second worst and missed at least 3-4 security patches while lesser known TCL and ZTE were found to have missed more than 4 patches.
The research further explains that the onus of missing security patches does not necessarily fall on OEMs, but even chipmakers are to blame. For instance, smartphones sporting MediaTek chipsets are often missing critical security updates because the chipmaker does not provide timely patches to the device manufacturers. In contrast, Samsung, Qualcomm and LG were found to have missed lesser number of patches.
The team at SRL has also developed a tool so that Android users can check the actual security patch-gap on their smartphones. Researchers have made an app called SnoopSnitch available on the Google Play Store which analyses the firmware of a phone to check for missed security patches. However, there are a number of permissions that a user needs to provide the app before it can dig into the firmware. These include – Network state access, internet access, calling and SMS access, and more. You can check the entire list of required permissions here.
Google has taken the research into account and is investigating the patch-gap issue.
Digit NewsDesk
Digit News Desk writes news stories across a range of topics. Getting you news updates on the latest in the world of tech. View Full Profile