Google deletes 29 ‘Beauty Camera’ apps that sent users pornographic content
According to Trend Micro, these apps had large number of downloads in India and redirected users to phishing websites as well as collected their pictures.
Highlights:
- Google deletes 29 malicious beauty camera apps from Play Store.
- These apps used to serve users pornographic content and collect their data.
- A large number of downloads were seen in Asia, especially in India.
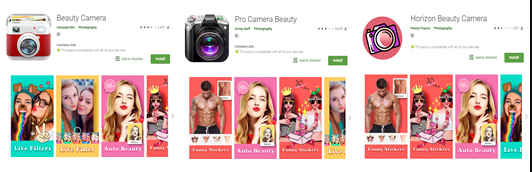
Google has removed 29 ‘Beauty Camera’ apps that used to collect the data, especially pictures, of the users who them installed on their phones. While some of these apps used to send pornographic content to users, others redirected them to phishing websites. Japanese IT security company Trend Micro says that some of these apps have millions of downloads, and a large number of the downloads originated from Asia – particularly India.
“We discovered several beauty camera apps (detected as AndroidOS_BadCamera.HRX) on Google Play that are capable of accessing remote ad configuration servers that can be used for malicious purposes. A user downloading one of these apps will not immediately suspect that there is anything amiss, until they decide to delete the app,” Trend Micro said in a blogpost. The top three apps: Pro Camera Beauty, Cartoon Art Photo, and Emoji Camera, each got over a million downloads.
For example, package com.beauty.camera.project.cloud created a shortcut after being launched. However, it used to hide its icon from the application list, making it more difficult for users to uninstall the app since it was not available for a drag and delete it. Furthermore, the camera apps were found to be using packers to prevent them from being analysed. Trend Micro has also shared a code snippet to show how the malicious app hid itself from the applications list.
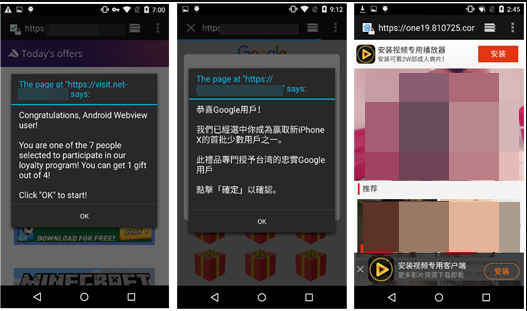
A number of these apps were also found to be pushing several full screen ads when users unlocked their devices, including malicious ads (such as fraudulent content and pornography) that will pop up via the user’s browser. “During our analysis, we found a paid online pornography player (detected as AndroidOS_PornPlayer.UHRXA) that was downloaded when clicking the pop up,” Trend Micro claimed.
Since these malicious apps looked as legitimate as possible, users found it difficult to determine where the malicious content was coming from. Some of these apps redirect to phishing websites that ask for personal information such as addresses and phone numbers. Some of the apps seemingly allowed users to “beautify” their pictures by uploading them to the designated server.
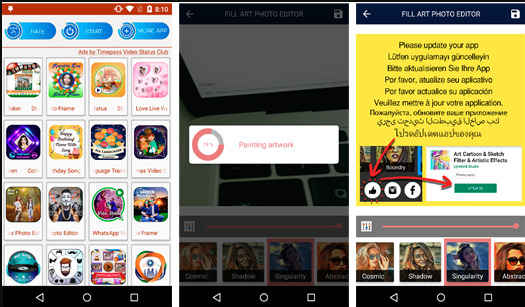
Trend Micro found that when a user uploads an image into edit in the app, instead of getting a final result with the edited photo, the user gets a picture with a fake update prompt in nine different languages. The authors can collect these photos uploaded in the app, and possibly use them for malicious purposes — for example as fake profile pictures on social media. Reportedly, these ‘beautify’ apps can also hide themselves like the ones mentioned above.
Related Read:
Quick Heal claims to discover fake apps on Google Play Store
Google removes massive trove of malware apps and shoddy reviews from Play Store
Digit NewsDesk
Digit News Desk writes news stories across a range of topics. Getting you news updates on the latest in the world of tech. View Full Profile