Windows 8: Secure at the deepest level

Windows 8 will come with antivirus protection running, but its real security benefit is vastly improved protection of low-level activities like memory allocation.
 Survey
SurveyIf every computer had antivirus software running, life would be tough for bot herders and cyber crooks. Their ability to orchestrate spam campaigns and denial of service attacks relies on a plentiful supply of unprotected computers. Windows 8 will put the squeeze on those creeps. It has antivirus protection built right in, enabled by default if no other antivirus is present. But the new security features at the very deepest level may be even more significant. To understand what Windows 8 adds, we need to look back at the evolution of operating system security.
The Story So Far
COM file programs for the original MS-DOS were laughably insecure by modern standards. DOS simply copied the program byte for byte from disk into memory and started it running. It made no distinction between code and data, so a buffer overrun attack could easily force execution of arbitrary code. Early file-infector viruses simply appended their own code to the program’s end and replaced the very first instruction with a jump to that code.
The EXE file format, still in use today, isn’t quite as open to manipulation. It does distinguish between memory areas used for code and those used for data. Windows XP SP2 introduced Data Execution Protection, which ensures that a memory area marked as data will never be executed. (Note, though, that it’s possible for a hardware backdoor attack to disable this feature).
Even with these enhancements, malware writers managed to craft attacks that could inject arbitrary code into trusted processes. Address Space Layout Randomization (ASLR), introduced with Windows Vista, made those attacks tougher by making it impossible for an attacker to predict where in memory a given code module would load.
Windows 8 Toughens Up
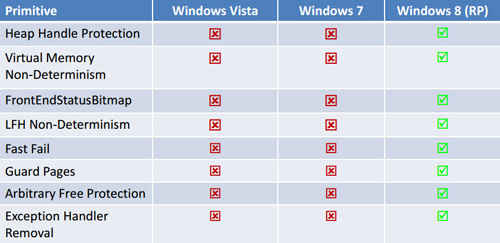
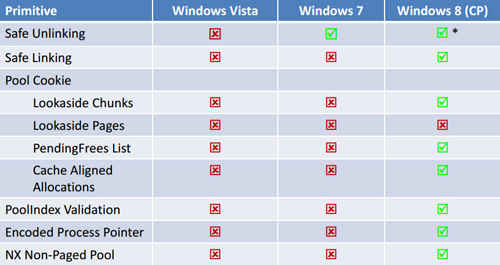
Despite all these protective features, malware attacks can still succeed in Windows 7. Windows 8 will block many such attacks by toughening up at the very deepest level—memory allocation. Many low-level memory functions have new safeguards in Windows 8, rejecting invalid input and adding a degree of randomness. “Guard pages” before and after in-use memory chunks prevent attacks that work by writing beyond the end of allocated memory. A new “Fast Fail” function lets a program terminate instantly if it detects memory corruption.
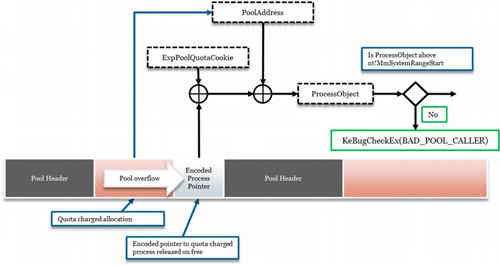
Windows keeps track of free and in-use memory chunks using a structure called a doubly linked list. Each chunk has an entry in the list with links to the next entry and the previous entry. Various attacks take advantage of this structure by changing the entries so they link to malicious code. That won’t work in Windows 8, though, because the pointers are protected.
ASLR makes it tough for an attacker to predict where a given code chunk will load in memory. Windows 8 also randomizes the allocation of smaller memory blocks within memory heap sub-segments. “Random” numbers generated by a computer aren’t random in an absolute sense, but in Windows 8 the random number algorithm is very much enhanced over Windows 7.
A Black Hat briefing by researchers Chris Valasek and Tarjei Mandt delivered an amazing level of detail about these and many other security enhancements found in Windows 8. The presentation slides and full paper are available online, for those with the chops to understand them. The overall point of these low-level security enhancements is to let Windows 8 perform its tasks efficiently while resisting all memory modification by external processes.
Windows 8 isn’t totally hack-proof. Valasek and Mandt detailed a number of areas that could still be vulnerable. After the briefing, I asked Valasek whether we’ll ever see a totally hack-proof operating system. His response: “No, that doesn’t exist. Not as long as humans are writing the code.” Even so, he noted, any attack or exploit that worked under Windows 7 will fail against Windows 8.
Copyright © 2010 Ziff Davis Publishing Holdings Inc