How to secure your Mac OS X
Macs aren’t hacker-proof! Here’s how you can fortify your Macintosh

The Mac operating system has long since been associated with an aura of user-friendliness and immunity to viruses and other malware. In fact, it is true that there are almost no viruses (in the sense of malware that can saliently infiltrate a computer without any user interaction) that affect a Mac OS (thanks to their file permission system). However there do exist vulnerabilities, as exemplified by the Rootpipe fiasco, which was patched after a whopping 6 months in April 2015 (exclusive to Yosemite and not for older versions), only to be exposed as an inadequate fix a few days later. There are also quite a few trojans, which usually piggyback on other software like video plugins.
 Survey
SurveyTheir installation however, requires tricking the user into authenticating it. Of course, it is true that the Mac operating system is comparatively immune to malware, but that is only because most malware targets Windows operating systems, and malware written for Microsoft Windows will not run on an Apple Macintosh. If you compare it with the number of different malware written for Windows, malware that targets Mac operating systems are a drop in a pond, but that is only because so many more people use the Windows operating system. So like it or not, Macs can and do get affected by malware and vulnerabilities, and are a far cry from being completely ‘secure’. Yet how many Mac users use anti-virus software?
Even the best Apples can have bugs
This anti-antivirus usage on Macs also means that even if there are malwares common on the Mac OS, hardly any of them get reported and as a result, carry on their infiltration without raising any flags. After all, an evil genius would design his/her malicious software to be as silent and unobtrusive as possible, in order to be detected as late as possible, post infiltration. Other than malware, security breaches on a Mac are also possible via third-party software like a browser. In particular, Adobe Flash and Java have been notoriously popular with malicious hackers thanks to their many holes and bugs, some of which allow the applet to gain access to the filesystem of the computer (if granted permission) but they are not the only culprits.
Now that you have an idea of the potential threats to your system, here are some ways you can fortify your Mac:
Setting Up Safely
Whether you’re setting up your new Mac or upgrading your OS, there are certain steps you can take the first time you start up the operating system that ensure minimal susceptibility to malware. There must exist at least one admin account and if you’re the sole user, as is mostly the case, that will be you. It is a good idea to create an unprivileged non-admin account in addition to this, to use for your everyday activities. Doing this will greatly reduce the amount of risk that you are exposed to, and even if something malicious gets in, it won’t be able to accomplish much. Other than a compromise of privacy, the main purpose of security is that you don’t lose your files, so backups are also a basic step for prevention of data loss. Take them regularly, and take them often.
Use your secondary account for your daily technology chores like reading manga or downloading songs. You can store your files without hassle and if ever you need to install something, you’ll be asked for the admin login details. On the one hand this does mean many more popup dialogues to enter credentials if you have relationship issues with software, but on the other, it gives you the freedom of being more exploratory while wandering the web. Also, set up your login screen to prompt for the password often if you leave your Macbook lying around.
Prevent a passerby peeping
Getting a Complete Firewall
Apple includes a firewall built in to the Macintosh, however that is an incomplete firewall because it blocks incoming connections but has no check for outgoing connections, which is what malware writers use for stealing data. A good two way firewall is one of the first pieces of software that one should install before wandering on the web. Sometimes software that you never suspected may be connecting to the internet without your knowledge, and without an outbound firewall, you will not know, nor be able to do anything about it. Software like Little Snitch 3 and Intego Net Barrier overcomes this limitation, allowing you to monitor and filter outgoing connections as well as incoming connections.
Purchasing Privately
The urge to shop is a powerful one, it can rival almost any addiction. Retail therapy is ever more accessible thanks to the modern ability to shop online and purchase with a few clicks. If ever this urge strikes you when you are using a public connection, like an airport or coffee house wifi network, your precious transaction data can be sniffed by an enterprising lurker. After all, what can be more lucrative information than credit/debit card numbers and passwords. Fortunately, most online transactions are secured by additional protocols so it is not super risky to order your groceries online before you board your flight. Besides making sure your connection is encrypted using https, you can use a virtual private network (VPN) to ensure that extra level of safety. VPNs offer an added layer of encryption and anonymity on the internet no matter when your entry node is physically located. Carrying out transactions and other sensitive communication over a VPN is sure to foil any attempts of sabotage from sniffed information.
Make yourself anonymous, use a VPN
Logging in Manually
By default, Macs are set to login automatically on boot, which makes things especially easy if you are the sole user of your system. While this is a great feature for the perpetually lazy, it is a potential security hazard for people whose system resides in a high traffic area and can be easily physically stolen. Once someone else picks up your precious Mac, all they have to do is open the screen and they are in. To disable this double-edged feature, open System Preferences, and inside Users & Groups you will find Login Options. Here you can set up your system to ask you to enter your user account manually every time you boot or open your Mac.
Encrypting the entire hard disk
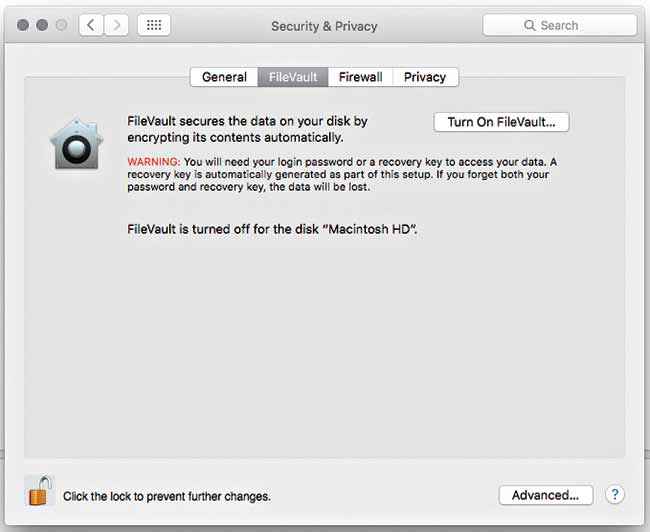
In the event that your Mac lies in the hands of thieves, a surefire way to protect your sensitive data is by having it encrypted from the start. Apple’s FileVault is their proprietary software that encrypts all that you tell it to with the XTS-AES 128 algorithm. To turn it on head to System Preferences > Security and Privacy > FileVault and after unlatching the lock in the bottom left corner, click on Turn On FileVault. Your account will need to have a password which you will enter to unlock your hard drive everytime you start up your Mac, which ties in to the previous point. However, in addition, every time you power down your Macintosh it will encrypt the entire hard disk making your precious data securely inaccessible to the prying penetrator.
Enable FileVault to secure your data
Auditing your Security and Privacy settings
Under System Preferences > Security and Privacy > General, it is a good idea to set your computer to allow the installation of apps only from the App Store and Identified Developers. In the odd case that you need to install some software that doesn’t have Apple’s verified developer signature, you will be asked to enter your admin password to authorize the one-off case. This step greatly reduces your chances of being affected by rogue malware, unless you blindly accept every exception request of course.
Make sure the bad guys don’t know where you are
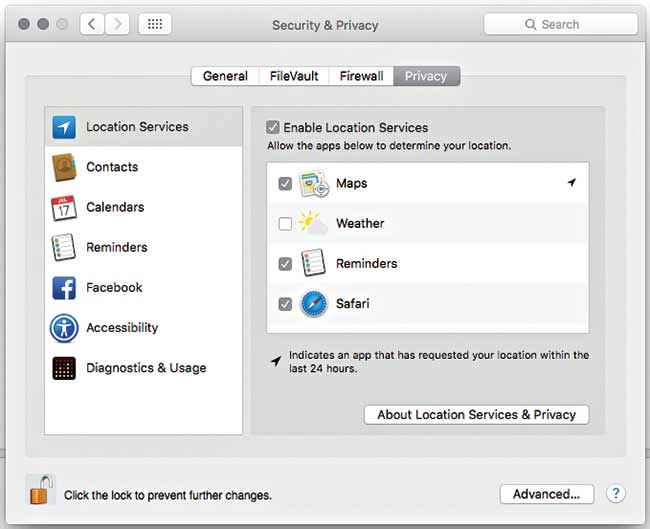
Also if you head to the Privacy tab on the same System Preferences page and selection Location Services on the left, the right hand pane will show you all the apps that are allowed to access your inbuilt location services and also the apps that have utilised this service in the last 24 hours. Keep a lookout for software that should have no business knowing where you are, it may be broadcasting your location to a malicious data merchant.
Regularly Updating your Software
Another very basic precaution that can prevent being the target of malware attack is regularly updating software as most known Mac vulnerabilities and holes target flaws on older versions of Mac’s OSX and other software. Security patches and fixes are rolled out officially in updates from the authoring company and so it is highly recommended to keep your operating system and all third party software up to date. This may sound obvious but many people skip updates out of data usage concerns or sometimes even pure laziness. While not always a must-have, software updates are almost always a good idea. Apple Store’s Software Update is the place where you can handle it all.
Keeping your Mac up to date
Staying away from Warez
Warez is a popular term for illegal peer to peer file sharing software that allows users to download and share pirated songs, movies, etc for free over the peer to peer network. Unfortunately, what most people don’t realize is that the drawback of this whole free file sharing system is that it compromises your identity online. Moreover, since it is illegal, the software will obviously not be verified and therefore it is a prime candidate for piggybacking malware or other malicious code. Other than the warez software itself, malicious code is often also added to the content files themselves, which unsuspecting users are in such a hurry to download. If you are a hardcore (or part-time) pirate who does not believe in contributing to the mega-corps, a safer (but still ‘illegal’) alternative is to use a bit torrent client over a VPN to ensure anonymity and encryption.
Installing ‘trusted’ and ‘reputed’ Antivirus software
Antivirus software is the single most effective solution against viruses, other than common sense safe browsing practices. It is important to note that life often offers u-turn plot twists for the unsuspecting wayfarer, such as the ‘trusted’ and ‘reputed’ antivirus software itself being the malware or adware. The problem is that even genuine antivirus softwares can only promote themselves and convey their capabilities so much via web content and marketing, and someone who isn’t in touch in the industry may not be able to discern the difference. Genuine players carve out their reputation over time so any good antivirus software will most likely be from a company which has been around for long and knows the field. Unfortunately, many unsuspecting users have fallen prey to software like MacKeeper, MacSweeper, MACDefender, and others. The common tactic is to scare users with annoying and unnecessarily exaggerated popups and ‘security warnings’ that are designed to make well-meaning but non-tech-savvy people download their software.
While there are almost no strict viruses that can wreck havoc in the Mac ecosystem (as of now) it is still a good idea to have an antivirus software like ClamXav to look over your files, especially those that are frequently exchanged with others. Even though a virus for Windows will not affect a Mac, it can certainly pass through, and ClamXav (or your favourite Mac antivirus) can detect and delete it for you.
Setting up ClamXav for Mac
Conclusion
It is well and good to take precautions but at the end of the day, the fundamental piece of the security puzzle is the user. A lot of trouble can be avoided with common sense and safe browsing practices. Congratulations! By choosing to use a Mac you have already dodged 99% of the malware out there. Thanks to statistics, along with the above mentioned steps, you may yet remain protected as you surf the wide web. A cliché worth repeating, better safe than sorry.
This article was first published in October 2016 issue of Digit magazine. To read Digit's articles first, subscribe here or download the Digit e-magazine app for Android and iOS. You could also buy Digit's previous issues here.