How to keep your online communication private and secure
Be it email, voice, or instant messaging – we’ll show you how to keep all your communications away from prying eyes.

Till about a couple of years ago, security, especially for normal folks, was not a big concern. But the Edward Snowden exposé revealed to the public for the first time, the extent to which our own governments are snooping on us and collecting our data. As if this wasn’t enough, there are also bad guys out there trying to break into our private channels of communication. So what do we do?
 Survey
SurveyThere are many points of vulnerabilities when you are communicating with someone, be it email, phone calls, or Whatsapp. This guide will teach you how to plug all these holes and secure all your means of communication.
Internet
Wi-Fi router settings
Your Wi-Fi is your gateway to the vast internet. It is also what makes you the most vulnerable. No matter what you do, a badly set-up router will remain a big potential source of leaks. Follow these steps to secure your router:
1. Change the default admin password and the SSID of the router. Go to 192.168.1.1 and login using the default username and password you’ll find in the manual (or try combinations of ‘admin’ and ‘administrator). If you want to go a step ahead, turn off “Wireless Web Access” too. This will make sure that only people inside your house with physical access via a LAN cable can change these settings.
2. Change the ‘Security mode’ under ‘Wireless Security’ to WPA2 Personal and use a strong password that doesn’t have any dictionary words, and has a good combination of alphabets, numbers and special character. WEP is old and relatively easy to crack.
3. Update your firmware regularly. New vulnerabilities keep popping up and new patches and updates are regularly released. You can do this either by going to your manufacturer’s site and looking for updates for your specific model or alternatively, checking for updates under ‘advanced’ or administration settings tab in your router’s control panel.
4. Go a step further and install custom open source Firmware like DD-WRT or Tomato. Most of the stock firmware on routers is clunky and includes many undocumented features and setting that can be exploited. There are many guides such as this one, available online that teach you how to install custom firmware on your router.
TOR
It’s ironic that a project that was started by the US navy has grown into something that is used by everyone from whistleblowers, to activists and privacy enthusiasts, to protect themselves and their identities from both the bad guys and the snooping government. TOR, short for The Onion Router, is right now being developed by a non-profit organisation dedicated to developing online privacy tools.
TOR is the best bet to secure all your communication going in and out of your machine
How TOR works and why it is so secure, is because it encrypts your data and sends it through random nodes on the network to the destination. This makes sure that anyone who is monitoring the traffic cannot trace any data back to its source or destination. To use TOR, follow these steps:
1. The easiest and quickest way to use TOR is to download the TOR browser for your operating system which is basically a modified version of Firefox with add ons and features that connect it directly to the TOR network.
2. Download and install the software from the project’s official site only.
3. Open “start TOR Browser.exe” and a new window pops up asking if you want to connect directly to the internet over TOR or want to configure the settings.
4. Novice users should select ‘Connect’ directly instead of trying to configure the browser manually.
5. Check your IP address from both ,your normal browser and the TOR browser, by going to www.whatismyip.com. If the IP addresses displayed are both different then you are all set to go. Browse the internet anonymously.
VPN
A VPN (or Virtual Private Network), tunnels your entire internet connection through a virtual local network. What this means is that all the data leaving your computer is encrypted and goes through a network of computers protecting your privacy from people trying to snoop on you. VPNs are a good choice if you are connected to the internet over some public Wi-Fi . There a number of free and paid VPN services out there which let are easy to download, install and use. Some of the good ones are:
1. OpenVPN server (free)
2. CyberGhost 5 (free)
3. Hotspot Shield (paid)
4. NordVPN (paid)
5. PureVPN (paid)
PureVPN ranks among the best paid proxy services. It is also one of the fastest and most secure VPNs out there.
Web browser proxies
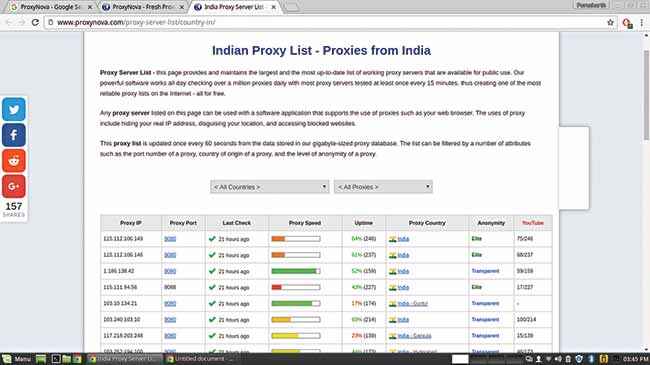
Web browser proxies don’t encrypt your complete internet connection but only whatever goes in and out of your Web browser. There are a number of websites online that keep a list of active proxy servers which you can use with your browser. Hidemyass and ProxyNova are two such sites which have a long dedicated list of active proxy servers, with each proxy’s speed, level of anonymity and country of origin listed. Choose one from these and set up your browser to use the same.
To use a Web browser proxy, do the following in your browser:
Firefox: Tools> Options > Advanced > Network > Connection > Settings
Google Chrome: Options > Settings >advanced settings > change proxy settings
Internet explorer: Tools > internet options > Connections tab > LAN settings > Use a proxy server
Once there, enter the port number and the IP address of the proxy server you are going to use. If the proxy requires a SOCKS connection, go to the advanced option and enter the settings.
ProxyNova has a comprehensive list of proxies categorised according to countries
Cloud storage
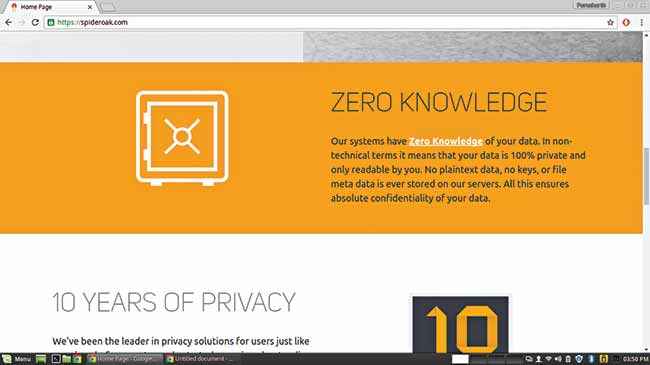
Looking for the most secure way to share your files over the internet? There are a number of cloud services available in the market. Almost all of them provide its users with some free storage. But which one do you choose when you not only want to protect your data from hackers but also be sure that not only hackers but also the company that is offering you the service doesn’t rat you out? SpiderOak and Wuaka are your top two choices. SpiderOak offers you 2GB free after which you can buy each additional 100GB for $10 a month while Wuaka gives you 5GB for free after which you can get 100GB for $12 per month. What these services offer and their more popular counterparts – Google Drive and Dropbox – don’t is, that they locally encrypt your file and then upload them. This makes sure that even the companies and their employees themselves cannot access the files they have stored on their servers.
SpiderOak prides itself in having “Zero Knowledge” about your data
You can also add an extra layer of security by encrypting the files before uploading and sharing them. There are a number of software out there which can do this like 7-Zip. Follow these steps to encrypt your files using 7-Zip:
1. Download and install the software from its official site.
2. Select the file(s) you want to encrypt and right click
3. Go to 7-Zip > Add to Archive
4. Set the Encryption method to AES-256 and enter a strong password that is long and a good mix of alphabets, numbers and special characters
5. Click on OK and Voila your encrypted archive is created.
Now share the file over cloud storage and share the password over some other medium like email or IM.
Email is one of the most used means of communication over the internet, specially for important and sensitive information. Unfortunately, it is also one of the most vulnerable ones. Email accounts are regularly hacked and emails are routinely intercepted. Your email provider keeps a record of all your emails, which they have to handover to government agencies in many cases. So what can you do to secure your email account? Read on to find out.
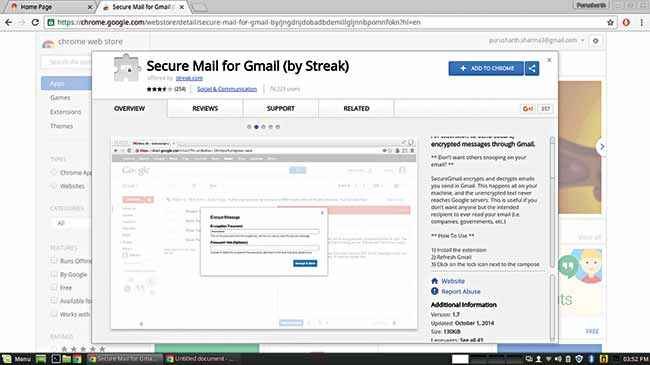
The emails you send don’t only contain the text and attached files. They also have a lot of metadata like your IP address. Email service providers such as Yahoo and hotmail don’t hide this information which make you more vulnerable. Gmail on the other hand hides your IP address and unlike the former two, also encrypts the content of the mail. But it still keeps a record of them. However, you can use the ‘Secure mail for Gmail’ chrome extension to encrypt and decrypt emails from right within your browser window.
SecureMail for Gmail is an extension that lets you encrypt and decrypt emails right from your browser window
If you want to go a step further use an email provider like RiseUp. RiseUp provides free email and is aimed at activists who need a secure and anonymous means of communication. The company uses a secure connection for both logging in and sending emails just like Gmail, and also has very strict policies in place to protect their customer’s privacy. But the thing with Riseup is that you need ‘two invite codes’ from existing users to signup. There are a number of other secure web services like Rmail, Sendinc and Hushmail which provided a free limited account and fully featured paid account.
Infoencrypt is a website that lets you encrypt the text of your email. All you have to do is enter the text and a strong encryption password and it will encrypt the text using a strong encryption algorithm. Copy paste the text into your email, and share the key separately with your recipient.
Instant Messenger
Instant Messengers are the quickest form of communication used in today’s world. There are a number of secure instant messaging applications and services out there. The best options if you want to secure your IM conversation are WhatsApp, the world’s most popular instant messaging service currently owned by Facebook, added end to end encryption to its application a few months ago. What this means is that the messages sent by you are automatically encrypted and decrypted only by the receiver. This makes it almost impossible for anyone snooping on your conversation to intercept and understand the messages. Even the company itself can’t decrypt your messages. WhatsApp offers more than enough basic security for the privacy conscious out there but it still lacks in places. The company still keeps a backup of your messages on its servers and maybe even logs your whole activity. Which means it is stored somewhere on a computer. And if the data is stored somewhere it can be hacked. Switch over to some other application if you want more security and privacy otherwise WhatsApp does just fine.
Download and use Pidgin: The application supports a number of existing messaging protocol, letting you use your existing accounts with it easily. Though the main feature is the end to end encryption which is activated only after the Off-the-Record plugin is added.
Chatsecure is another free application for both iOS and Android that helps you keep your messages private. It does this by using various open source cryptographic libraries along with OTR and Tor.
Silent Text is one half of the Silent Circle software package that lets you send secure , encrypted voice, video and text communication. The software comes at a price of $12 per month and is one of the best in the market
TextSecure for android and Signal for iOS are a pair of secure SMS / IM applications by the company WhisperSystems. TextSecure integrates with your default android messaging application and automatically encrypts the message you send to another TextSecure user. Signal, the iOS application, does not integrate with the system like its android counterpart does, but works the exact same way. Also the two apps can be used to securely communicate with each other. Both the applications are freely available on Google play Store and iOS app store.
Telegram is another good option for people looking to securely communicate with their friends and families. The creator of the application describes it as “WhatsApp but encrypted, cloud based and faster”. The application has also the features that a good IM app has like sharing media, and messaging upto 200 people at once, but it is its security features that set it apart. The application not only uses end to end encryption making your communication safe and secure, but also has a secret chats feature that leaves no trace of your communication on the Telegram servers. You can also set a time for automatic deletion of your messages.
Call
The Edward Snowden leak brought NSA’s infamous PRISM program to the limelight, making the world realise the extent of invasion of privacy that governments have been involved in. So how does one make a phone call without being afraid that each and every word that you are saying isn’t being recorded somewhere? Simple. Use one of the following applications:
Redphone (Android only) – An application by the same WhisperSystems who developed TextSecure and Signal, Redphone let’s make you free encrypted calls through your android phone over the internet. The application encrypts everything from your data to the metadata attached to your call, shutting out everyone trying to eavesdrop on the conversation, be it the government or a hacker.
Silent Phone (iOS and Android) – The paid application lets you make secure and encrypted phone calls between Android and iOS too. Also, the Silent Phone user can call non-users with it, where only one side of the conversation will be encrypted.
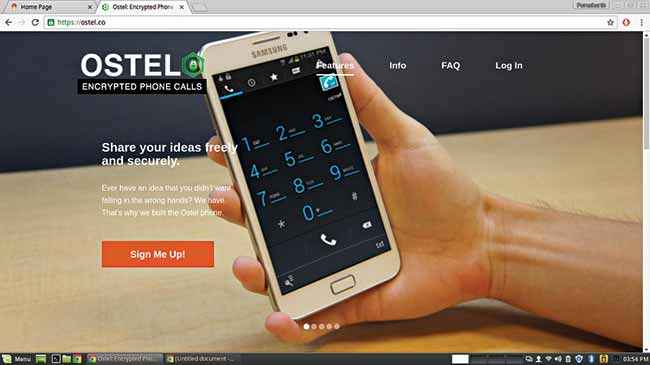
Ostel (iOS and android) – Another paid application, Ostel uses Open Secure Telephony Network to make encrypted calls across platforms. All you have to do is create an account on Ostel.co and download the application for your device (CSipSimple for Android, Groundwire for iOS and PrivateGSM for Blackberry and Nokia for those who still use them). Once downloaded you are all set to make secure encrypted calls to other Ostel users.
Ostel lets you make secure and encrypted phone calls between android and iOS
Video conferencing
Microsoft’s Skype and Google hangout, two of the most used video conferencing tools, both encrypt your communication making it safe from prying hackers. But your whole communication goes through the servers of the companies where they are also logged and stored. This information in some cases could be revealed to the government agencies.
The best and most secure video conferencing tool out there right now is Bitmessage – a complete email suite. Based in part on the ‘bitcoin principle’, the service encrypts all its communication data and metadata, and can also be used with TOR. You can download it’s official client called PyBitmessage with a built in video conferencing tool.
Even though Skype encrypts your communication, it still stores the data and logs on their servers making you and your data vulnerable
Facetime, the competitor by Apple provides end to end encryption, but the company is known to regularly comply to court orders and government agencies.
Also, there are a number of paid software out there like OmniJoin and BlueJeans that provide safe and secure cloud based video service.
This article was first published in October 2016 issue of Digit magazine. To read Digit's articles first, subscribe here or download the Digit e-magazine app for Android and iOS. You could also buy Digit's previous issues here.