Basics of cyber security and tips to be safe online
Here we list down some common sense best practices that’ll go a long way towards keeping you safe online

You might feel that protecting yourself against cyber attacks is a job only for specialists, but that isn’t really the case. Also, securing yourself isn’t about throwing money at the problem either. Sure you can choose to shell out a few bucks initially for the sake of convenience you don’t really need to.
 Survey
SurveyOf anti-virus software and firewalls.
The most basic step anyone could take is to install an anti-virus software. For a long period of time, the understanding was that only careless Windows users, who had no inkling about separating the fishy links from the legitimate ones, and who roamed the weird and unsafe corners of the internet, needed to have an anti-virus program. But in today’s age of zero-day vulnerabilities and large-scale hacking, this notion is a dangerous one to spread.
A zero day vulnerability refers to a hole in software that is unknown to the vendor and has the potential to be exploited by hackers in the form of infiltrating malware, spyware or illicit access to the software user’s personal details and information. Such security loopholes are exploited by hackers before the vendor is made aware of them, and has led to many zero-day attacks in the past. For example, in March 2013, Oracle discovered two zero-day vulnerabilities, of which one was actively used by hackers in targeted attacks. The vulnerability could be exploited remotely, without any form of authentication to kickstart it in affected machines. Since the risk applied to both Windows and Mac devices, the number of possibly affected devices could run into millions.
There’s also the massive Elderwood project, a platform that has used, as researched and reported by Symantec, an “unlimited number of zero-day exploits, attacks on supply chain manufacturers who service the target organization, and shift to ‘watering hole’ attacks” on websites likely visited by the target organization”. Their biggest target was Google, back in 2012. Though no data was stolen or compromised, these findings brought to light the increasingly sophisticated techniques used by hackers to bring even the biggest corporations to their knees. So there’s no doubt that if a player as big as Google can be a target, then even the most careful of users are vulnerable to these loopholes, and the first and foremost step that anyone who owns a PC, laptop or smartphone should take is install anti-virus on their device.
An example of an anti-virus software
While choosing your anti-virus, its best to go for the big names. Windows has a built-in Windows Defender, though most security experts recommend installing additional AV software. In its defence, since Widows Defender is free and built-in to Windows 10, it doesn’t harass you with pop-ups and requests for money, and is lighter than some competing antivirus solutions – making it the preferred basic line of defence by a lot of people.
Yet, if you’re constantly installing new software and engaging in high-risk behaviour, paid anti-viruses like Norton, McAfee and Kaspersky etc are known for their detection rates, and are considered safe bets. The same would go for Macs, and Linux is known to not require an anti-virus, though that largely depends on how technically informed the Linux user is, which a majority are. Free anti-virus solutions like Avast, Avira and AVG are just as good as the paid ones except you don’t get priority support. The core detection engines offered by free ones are the same as their paid versions in most cases.
Though installing anti-virus software is the recommended way to go, enabling a Firewall on your device also goes a long way, though it can’t provide the same level of protection an anti-virus would. A software Firewall, just like a device-based hardware Firewall, would filter information coming through the Internet into your system. If an incoming packet of information is marked by the filters, it is not allowed through.
In large corporate institutions or any business that has a small to large private network it wishes to protect from outside attacks, the main function of a Firewall is that it stops anyone on the outside from logging onto a computer in the internal network. Since most home networks would not be subject to such an invasion, a Firewall might not perform the exact way you’d expect it to. Nevertheless, when it comes to cyber-security, more is merrier, and you can never go wrong with a Firewall. ZoneAlarm and Comodo are two well known free solutions you might want to try out.
Before you plug in that usb stick…
There are several more precautions one can take to prevent malware from external sources. Making sure the software you install is from a verified source goes a long way. A lot of malware is installed as a result of people not taking care about the kind of software they give permission to run on their systems. Whenever downloading any such thing, go to the verified site first, and avoid using any external links that redirect you to the “official” site. Even if you don’t use the internet much, viruses and malware now have a way of spreading through pen drives and external HDDs.
This doesn’t need much effort from the hackers’ side – they’ll simply disguise the virus as an executable having a recognisable name; even if the virus might not be a software, the common trend in many infected disks is to create a shortcut that contains all your files that were previously visible in your external disk. When you try to open any of the folders, the virus automatically gets executed and infects your PC. The best and only way to get rid of such viruses is to get your anti-virus to scan the infected drive and have it weed out the virus. The best way to go would be to scan any external drive that’s inserted into your device, no matter how trusted the source is.
Where’s that free Wi-Fi?
One particularly prevalent and unavoidable issue is the use of public Wi-Fi hotspots. The very convenience that makes public Wi-Fi so attractive is what is probably its downside. The fact that public networks require no authentication to establish a connection is what allows hacker to get unrestricted and unlimited access to unsecured devices on the same network. Since there is no password or passphrase to encrypt the information being sent to and fro between the router and the device, any hacker can use software to intercept those signals at which point they can see everything on a fellow free WiFi user’s screen. Such “sniffer software” intercepts the traffic between the router and device to filter out important information.
These unsecured networks can also be used to plant malware in another network user’s device if file-sharing has been enabled. Another popular method used by hackers is to set up rogue Wi-Fi hotspots with generic names, hence fooling unassuming users into connecting to these networks, following which their information can easily be collected.
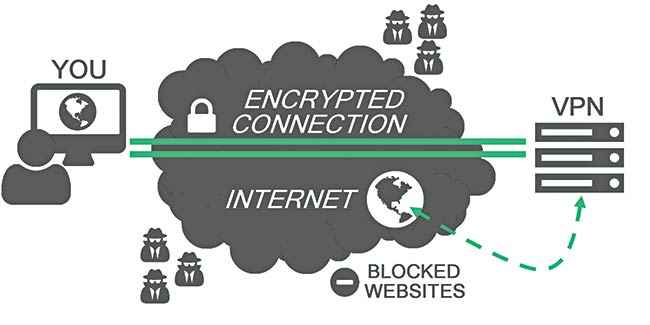
Considering that necessity generally overrides such concerns many times, one can take certain basic and inexpensive steps to avoid any mishandling of personal information. If you find yourself needing to connect to public Wi-Fi networks frequently, it’ll be worthwhile to invest in a Virtual Private Network (VPN). A VPN is a private network that enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network.
A bonus is that VPNs will allow you to access blocked and filtered content, hence providing a better internet experience. Most trustworthy VPN services require a monthly subscription of a few hundred rupees, and are certainly worth the expenditure if you’re regularly using public networks.
Some great VPNs in India are Private Internet Access, Torguard, CyberGhost VPN and TunnelBear, which cost between Rs. 400-800/month. If your usage of public networks is infrequent and you do not need to visit websites with confidential personal information, credit card data and important emails, enabling the “Always Use HTTPS” option, or simply installing browser add-ons like “ HTTPS Everywhere” is useful and does the trick. Another useful tip is to turn off device sharing on such networks, so that malicious devices cannot access yours, and enabling the Firewall, as discussed before.
Understanding how a VPN works
“What happens if I click on this pop-up…”
Once you’re on the internet, a lot of what happens to your computing device is in your hands. How you deal with spurious links, banners and pop-ups will determine the health of your device.
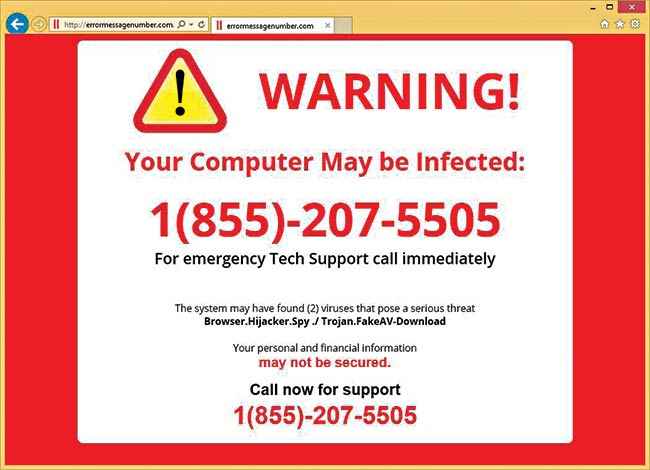
It goes without saying that many of the banners, ads, pop-ups and emails that you view and receive on the internet are scams. Many of these popups, which look like legitimate posts coming from your email provider, favourite social media websites or e-commerce sites are generally spurious and fake versions. Many a times these pop-ups pretend to find viruses and malware on your device and “report” them.
Entering your personal details while executing any kind of operations on these imposter websites is only going to lead to hackers picking up your details, and you’ll have only yourself to blame. This process of tricking you into sharing your information is known as phishing. And software that engage in this kind of behaviour are known as scare-ware. If such software go a step further and demand money for making your system function properly again, they are known as ransomware.
Beware of such pop-ups
In a very common practice, many users receive mails from seemingly trusted sources, stating that the said user has provided incorrect information for important documents, and that they will have to resend their information to revive a suspended account or some similar scare tactic. People will end up going to the imposter version the hacker wanted to redirect them to, and end up providing bank account and email account details willingly. In the case you’re looking to visit any such website, always visit the encrypted and original website by using a popular search engine to obtain the website details. Big providers like Google, Yahoo! and Bing always give correct and accurate results, and can be trusted to provide the original links for certified websites.
In other methods, flashy banner ads on websites are created as sources of malware. Clicking on them automatically gives them permission to install the said malware onto your device. In most cases, the malware simply logs keystrokes and sends them to the hacker, allowing them to monitor your data and thus making it extremely easy to get access to your private information. While your anti-virus should help prevent the download and execution of such malicious software, it’s better to be safe than sorry and just not click on these banners.
Is your password “123456”?
When it comes to how you store your confidential data, you need to take a hard, long look at your passwords for your various accounts. The dilemma for most people is choosing between a weak password that is easy to remember and is easy for hackers to crack, or a strong password that is hard to remember but much tougher for hackers to guess, even with their fancy-schmancy algorithms. We’ll assume you go with the latter, since no security conscious individual would ever choose the former. First and foremost, never lift passwords from a dictionary, even if they are multiple words one after another. Such passwords are easy for hackers to figure out using a dictionary as a source dump for a brute force attack.
To further secure your password, use special characters and a mixture of lowercase and uppercase letters, as well as numbers. In addition, longer passwords are better than shorter ones, since they become harder to crack with each character added. A rule of thumb is to keep a minimum length of 10 characters. Having said that a brute-force attack to guess the password will always succeed if enough time and processing power was available to the attacker. So, it is always recommended to change the passwords often. Try to keep the timing between every 4-6 months.
Then there’s the general guidelines. Avoid using standard and repetitive sequences, and absolutely NO personal information should be included. If the hacker happened to have your personal information, don’t make it easier for them to crack your password. And if you do happen to create a tough-to-remember and uncrackable password, make sure NOT to reuse it for any other account. As tempting as it sounds, it can have severe consequences for you in case the hacker knows the details of one account. This does bring us to the point of remembering your passwords for ALL your accounts, which numbers runs into tens for those active on the interwebs. It’s considered smart to not write your details on paper, and instead use an encrypted password manager.
A password manager requires you to remember only one master password, and the rest and generated and stored by the encrypted password vault itself. LastPass Premium and Dashlane are considered good alternatives for those willing to shell some money, while LastPass and LogMeOnce are available for those on a budget. Still, it’s recommended that you invest in a paid password manager.
LastPass Password Manager on a Mac
None of these will work if you’re giving out your password left, right and center. Avoid sharing your password, and even if you have to, please, for the love of glob, don’t email it to the other person. It’s unnecessary and you will have only yourself to blame for such an egregious error. In other etiquette, avoid leaving your accounts logged in on public terminals, and make sure no one’s watching when you’re typing your details. These common and basic steps will go a long way in securing your cyber life.
In case your password is hacked or leaked in a data theft, one way of being notified of any incorrect access is if you’ve enabled multi-factor authentication, which is extra layers of security that require not only a password and username but also an external key that only the user has on them, with the key generally being some sort of physical token. In most cases, it’s a one-time password sent to your mobile phone, and in rare cases, another email ID (the latter is an unsafe choice in the eventuality that the second account has been compromised). While this method has its own drawbacks, it’s a good idea to have two-factor authentication enabled across your accounts.
We mentioned zero-day vulnerabilities earlier, and talked about how anti-virus software is a great way to patch those up but be sure to keep your AV software up to date. Seeing as how many hackers might misuse the patch release notes to explore those vulnerabilities on unpatched machines, it’s important to install such software updates as soon as possible after they’re available. Browser plug-ins also form a huge part of the issue, and to be completely sure that you don’t have outdated browser plug-ins, visit your browser’s plug-in check website.
A lot of these methods are basic common sense and no more. If you feel like you need a little more information for platform-specific devices, read more security articles here.