Xiaomi responds to eScan’s allegations of MIUI’s vulnerability

eScan released a 36-page report claiming Xiaomi’s MIUI is ‘un-intentionally vulnerable’ and contains multiple flaws that could compromise user’s data. Xiaomi has reverted insisting that this is not the case
eScan, a Security Solutions company has released a research report claiming that Xiaomi’s MIUI custom ROM has multiple flaws that jeopardize a user’s data and its security. The report claimed that Xiaomi’s uninstall procedure along with the Mi-Mover feature were a serious cause of concern as they were flawed and could potentially give unrestricted access to a user’s data. Most of the tested apps were deemed exploitable after being restored using the Mi-Mover app.
Xiaomi, in an email to Gadgets 360 said that eScan’s allegations are only valid if a perpetrator has physical access to an unlocked Xiaomi device. Xiaomi further stated that it recommends its users to set up a lock screen security feature such as a PIN, password or/and fingerprint sensor. The report, in line with Xiaomi’s reply, stated that another line of argument is crucial for the vulnerabilities to be exploited which is “Physical access to the victim’s phone is required”. However, eScan asks what precautions do Xiaomi device users have to take into consideration while handing over their devices over to service centre employees? And with anti-theft security mechanisms affected, questions how Xiaomi users would ensure their device doesn't get stolen?
Image credits: eScan research report
The report also expressed that the introduction of the said threats was introduced unknowingly by Xiaomi and they alone cannot be held responsible. The app developers are equally responsible for not considering the possibility of their app data being cloned. The report was summarised as,“Xiaomi’s system apps have unknowingly introduced multiple flaws into the functional working of most of the apps. The functional aspects of Anti-Theft security apps and Android for Work apps are affected by the un-install procedure implemented by Xiaomi. Furthermore, the MI-Mover app which assists in user-data migration also poses significant threats to the installed apps.”
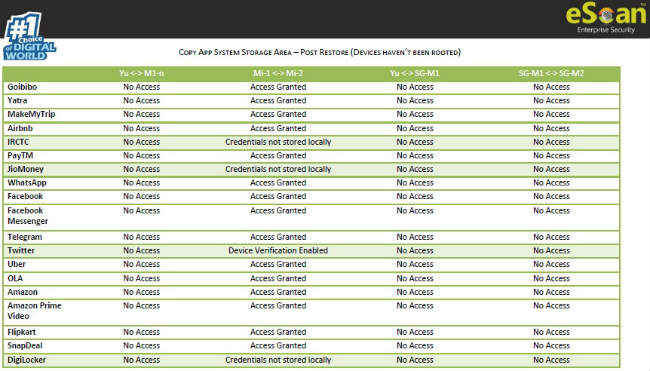
The most worrisome part is the plethora of apps that have been considered secure are now vulnerable on Xiaomi’s MIUI albeit, someone gets physical access to the device. Some of the apps tested and considered vulnerable in the eScan report are: Goibibo, Yatra, MakeMyTrip, Airbnb, PayTM, WhatsApp, Facebook, Facebook Messenger, Telegram, Uber, OLA, Amazon, Amazon Prime Video, Flipkart and SnapDeal. Nearly all of the above-mentioned apps give unrestricted access upon restoration and thus could cause serious damage. Most of these apps developers have been contacted and notified about this and some have already issued patches and updates for the same. JioMoney, IRCTC, Twitter and DigiLocker were some of the apps that were not so severely affected as they asked for credentials or sent an OTP every time a user tried to log-in.
Facebook’s security team response was, “As part of exploiting the issue you describe, someone needs to take control of a user's mobile phone and get that phone in an unlocked state. This is a very high barrier to entry and seems unlikely to happen commonly, making this more of a theoretical attack. The protection in this case is to not allow someone to steal and unlock your phone".