Android 4.2’s built-in malware scanner tested, detects only 15% of threats

Google’s choice to go with a more open app model for Android has invited nefarious people all over the world to develop exploits for the platform. Various anti-malware services have launched on Android, but Google stepped into the ring just recently when it added an app verification system to Android 4.2 Jelly Bean. How well does it work? That’s a question researchers at North Carolina State University (NCSU) have attempted to answer. The results are not pretty.
 Survey
SurveyOut of 1260 malware signatures, Google’s native verification system in Android 4.2 detected only 193 — that’s a little over 15%. While this sounds laughably bad, there’s a little more nuance to the numbers.
What’s supposed to happen
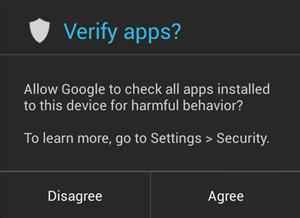
The first time an app is installed on Android 4.2, a message pops up asking the user to enable app verification. This will probably be the last time most people see the app verification screen, but it will be silently working in the background. It even has a very Googley approach: Unlike most third-party anti-malware services, this is an entirely cloud-based solution.
When an app is installed, Android gathers a few pieces of information about it. It will aggregate things like the package name, size, and SHA1 hash value. This data is sent off to the Google servers, where it is compared against a database of potential threats. The result is sent back down and the user gets no feedback if the app is clean. If Google finds something suspicious, the device will block the installation.
Since all apps installed on Android go through the same package verification (there is no such thing as a silent install on Android), Google’s system should be in a perfect position to detect all threats.
What’s actually happening
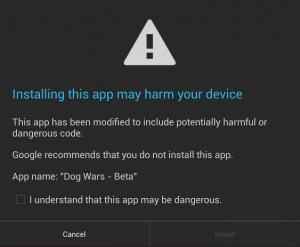
The NCSU team found that Google actually fails to detect a great many malware packages that the third-party apps handle just fine. Just like desktop malware, there are usually updated and slightly modified versions of the same basic bit of malicious code. In some cases Google could detect the original variant, while missing all the new ones. But why?
Google’s verification system relies almost entirely on SHA1 values and the package name to determine if something is malicious. This is a very limited approach because malware authors can easily change the checksums without making any other alterations. Google just isn’t acquiring enough information to do in-depth analysis.
The third-party apps are running local checks on apps as they are installed, which is probably why some of them have perfect or near-perfect detection records in the NC State tests. Google is doing all the work in the cloud, and it doesn’t want users waiting on a response from Google’s servers while it verifies apps.
A potential benefit to this system is that Google can update the malware fingerprints on its servers at lightning speed without pushing updates down to all users. It will also be incredibly straightforward to target a specific threat in the future. Basically, the kind of widespread malware attacks we saw in the Play Store a few years ago could be stopped before they ever got going.
Behind the numbers
I’ll be the first to admit that these numbers sound bad — they are bad. If Google is going to go out of its way to add malware detection to Android, it should have done a more thorough job with it. However, many of the malware samples tested by the researchers are complete non-issues at this point.
Take the so-called DroidKungFu Trojans. These nasty little bits of code are intended to root a target device and give control of it to a remote server. Yeah, it sounds really terrible until you realize this malware relies on an OS exploit that was patched at the system level over two years ago. There is just no reason for Google to bother scanning for this. No phone with the app verification system will ever need to worry about any of the nearly 500 DroidKungFu samples tested.
It’s the same story with a few other pieces of malware. Android is no longer susceptible to many of these old attacks, but the researchers checked anyway. This was just scientific thoroughness, but I feel like it should have been pointed out in the results that many of these exploits are now neutered.
One issue uncovered by the study is the way Google is handling SMS Trojans. These apps use the Android permission system to message premium rate numbers and rack up huge charges. SMS Trojans are usually found in obscure Chinese app stores, but Google detected almost none of them. This likely has something to do with most of Google’s certified device users (i.e. non-Chinese) being at little to no risk of catching a SMS Trojan.
Time to panic?
In a word: no. The time has not yet arrived to smash your Android phone and live off the grid up in the mountains. Google has been implementing security measures like app verification and the Google Play Bouncer to improve security. These systems have improved security, but the problem was never as bad as some news headlines made it seem. Pirated apps hosted in suspicious Chinese app stores are filled with malware, but that’s not something you need to fret over.
Apps you get from Google Play are almost certainly safe these days. As for the somewhat shady things they do with your data, that’s another matter entirely. Google is trying to get the tools in place to protect Android users going forward. For the time being, this is all a placebo. That goes for Google’s approach, and the third-party apps alike.
Now read: Demystifying Android 4.2 Jelly Bean
Copyright © 2010 Ziff Davis Publishing Holdings Inc