Is Your Network At Risk Of Hackers?
You’ve secured your office network with the best of hardware and software layers to ensure it is safe from the prying eyes of a hacker. But, is there a weak link in that security chain? Well, the humble printer might just be the next target and the impact can be catastrophic. Let us explain.

With traditional vulnerability points in an enterprise network becoming increasingly challenging to hack, the next wave of break-in attempts might stem via the most unexpected source. In fact, it’s already happening. The question is, are you guarded against it?
 Survey
SurveyNobody ever suspects the office printer. Fifty-six percent of enterprise companies leave printers out of their security strategy. Research conducted by the Ponemon Institute reported that 60 percent of companies surveyed had a data breach involving printers, requiring an average of 46 days to resolve a cyberattack. In another survey, 80 percent of companies indicated that IT security is important to business processes; but just 59 percent of those companies stated that print security was important to them.
Here are five ways print security risks can unleash some serious damage to your business
Compromised network
Even behind the firewall, many devices on a network may create a new access point to the entire network. When printers are overlooked in a comprehensive network security plan, that point of entry can be very welcoming to hackers, who can cause catastrophic consequences once inside the network.
When a hacker takes-over an unsecured printer
When hackers gain access to unsecured printers, they wield all the power for destruction. Your printer could become a possessed machine, printing random jobs, transmitting foreign faxes and changing all of its settings. Printers are also prime targets of denial-of-service (DoS) attacks.
Data breaches
Unencrypted print data is a hacker’s dream. If data transmitted to a printer is unencrypted, it shows up as clear, legible text. If hackers want access to this data, it can be captured and read using a standard PRN reader.
Unattended print jobs
Abandoned printouts can sit for days in the printer’s document tray or end up littering the copy room. Nosy employees can sneak off with confidential information inadvertently left behind. This information leak also makes a company liable for regulatory compliance failures.
Access to mobile devices complicates it further
As computing devices on the network expand to include mobile devices, it is more challenging to provide network authentication and secure access to printers. Even if the printer is on a secure network, the mobile device might be compromised, creating potential back-door opportunities for a hacker.
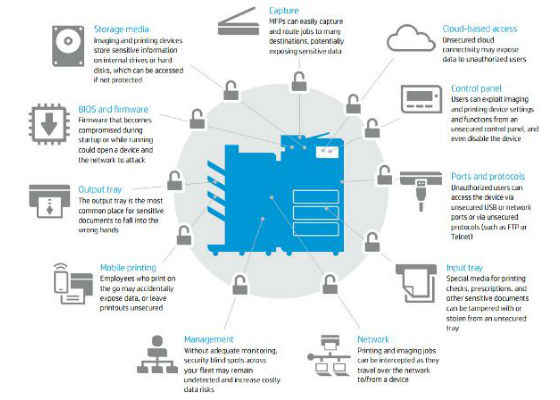
Imaging and printing vulnerability points
Getting started with print security: Protecting your business against such threats require a 360 approach towards security, ensuring there are no loop holes left open for a potential exploit. However, here are a few guidelines that can go a long way towards protecting you from vulnerabilities around print security.
- Make sure that computing devices use only encrypted communication protocols, and disable unused ports and protocols on the printer.
- Put a system in place that erases or destroys the printer’s hard-drive data as part of removing the device from circulation.
- Support at least one form of user authentication (preferably two or three), and consider the implementation of pull printing for print environments with a high volume of confidential information or compliance requirements.
- Ensure printer firmware is current and only legitimate firmware is ever loaded.
- Use a fleet management tool to centrally manage, monitor and remediate devices to ensure compliance with security policies.
- Make sure all data between both desktop and mobile devices is encrypted to be certain the print-related data is fully protected from man-in-the-middle attacks.
- Engage a security consultant. Don’t be afraid to tap experts when there are gaps in your staff’s knowledge about certain issues. Printer security experts can help you create a strategy that works for you.
- Conduct an assessment. Is your company really at risk, and to what degree? Assess your current security measures to see if they’re up to scratch. Take this free survey to see where your weaknesses may lie.
- Develop a plan. Help secure your print fleet and schedule necessary appraisals and evaluations to keep that plan actionable as technology, and the hackers who want access to it, evolves.
Read more about HP’s secure printing solutions to find out how you can deploy the most adequate print security strategy for your office network.