Meltdown and Spectre flaws: What’s really at stake? Who is affected? How are companies planning to fix them?

Intel’s Meltdown bug will affect Intel Processors going back more than 10 year, and the Spectre bug will affect every device running on Intel, ARM and AMD chips. While the Initial fix is out for Meltdown on all desktop OS platforms, there is no fix for Spectre.
If you have been reading any tech news lately, you will see almost all tech websites are plastered with a critical “Intel flaw” news which could possibly lead to a security breach. More importantly, if you do get an OS update to resolve the matter, your system will get a performance hit from anywhere between 5 – 30 percent taking into account other parameters attached to it.
Is a decade old ‘flaw’ is finally coming back to bite us? We take a step back and try to give you a gist of what has transpired in the very first week of 2018, which might unsettle you a bit or more.
Two days back, various security researchers took notice of a series of changes being made to Linux systems. The comments on the update patch were highly redacted which led to further confusion on the matter. It was then reported by multiple sources that Microsoft is also ready to push a similar update to fix some critical issues. As of yesterday, further digging by security researchers across the globe resulted in a conclusion that the issue lies with Intel processors.
The problem lies with Intel’s x86-64 architecture itself which meant all processors made by the company in the last decade or so are venerable. The issue became even bigger and rather grim when new info on the matter surfaced, putting AMD and ARM right beside Intel in the red zone.
Double Trouble
New information on the matter finally revealed that the issue was discovered last year by a group led by Google’s Project Zero team in collaboration with other researchers from various universities. They discovered a problem with a processor's speculative execution. Speculative execution is the lay term given to the method where a CPU predicts which calculations it needs to do beforehand based on what is happening and what it might need to do. The CPU then performs those tasks in parallel. This is done essentially to enhance the performance of the CPU. However, out of the entire processed data, not everything is required in the end. Now, the CPU does not erase this data and fragments of it remain in the system’s cache memory from where it can be accessed. This cached data can then be fetched from the protected kernel memory before it performs any security checks on it.
The problem with Intel processors starts here. The thing is that the Kernel layer is basically the layer which works as a middle man to the processes and the hardware. If a process let’s say Chrome wants to write something on the hard drive (save file), it will ask the kernel layer (part of OS) to do so. The OS will instruct the CPU to follow up and once the task is done and give back the control to Chrome process. Ideally, this Kernel layer should be hidden from the process, but the Intel flaw allows the malicious software to see through, thus giving access to it.
There are a few more steps to this and it ends up as bug named Meltdown. This particular bug affects only Intel processors and is well put together by Ido Naor, Senior Security Researcher at Kaspersky Lab’s GReAT Team along with Jornt van der Wiel, Senior Security Researcher, GReAT
“Applications installed on a device generally run on ‘user mode’, away from the more sensitive parts of the operating system. If an app needs access to a sensitive area, for example the underlying disc, network or processing unit, it needs to ask permission to use ‘protected mode. In Meltdown’s case, an attacker could access protected mode and the core memory without requiring permission, effectively removing the barrier – and enabling them to potentially steal data from the memory of running apps, such as data from password managers, browsers, emails, and photos and documents.”
If you thought Meltdown is bad, then you should probably sit down (literally) for Spectre as this bug is a set of attacks which essentially can snoop across all devices and all platforms.
“Spectre attacks involve inducing a victim to speculatively perform operations that would not occur during correct program execution and which leak the victim’s confidential information via a side channel to the adversary” – Spectre paper.
There is still little known about the bug and the confidentiality on the matter is being maintained to keep the information away from hackers. Theoretically, researchers say that this is much harder to exploit in real life, but the problem is that it is even harder to mitigate and currently there is no fix for the issue. However, there is no reported exploit as of now either.
But, a fix is on its way
In a report published by The Register, it was mentioned that the details of the vulnerability are under embargo which means that the issue was known. So, why did nobody report it until now? Well, the simple answer is that to keep users (both commercial and consumer) out of the harm’s way as the flaws were being researched upon and OS-makers were were working with chip makers to make a patch to resolve the issue.
The good news is then that initial patches for Intel’s Meltdown bug are out and available across all three major OS platforms. If you haven't received the updates yet, check respective websites for the same. Also, update your browsers to the latest versions as Firefox and Google Chrome have already initiated respective patches. In all of this AMD seems to be in the safe zone as the bug does not affect AMD powered systems because of the architectural differences between Intel and AMD processors.
However, the Red team (AMD) along with ARM and Intel will be on the lookout to figure out a way to fix the issues presented by Spectre bug. While the bug is hard to exploit, it is still a bug and sooner or later, chip manufacturers will have to do something about it.
Here is what companies affected by the two bugs had to say on the matter:
Intel
Here is what Intel had to say. You can read the full statement here.
“Recent reports that these exploits are caused by a “bug” or a “flaw” and are unique to Intel products are incorrect. Based on the analysis to date, many types of computing devices — with many different vendors’ processors and operating systems — are susceptible to these exploits.”
Intel adds, “Intel is committed to product and customer security and is working closely with many other technology companies, including AMD, ARM Holdings and several operating system vendors, to develop an industry-wide approach to resolve this issue promptly and constructively. Intel has begun providing software and firmware updates to mitigate these exploits. Contrary to some reports, any performance impacts are workload-dependent, and, for the average computer user, should not be significant and will be mitigated over time.”
AMD
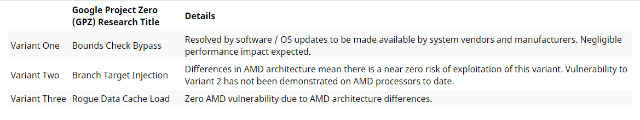
“When AMD learned that researchers had discovered a new CPU attack targeting the speculative execution functionality used by multiple chip companies’ products, we immediately engaged across the ecosystem to address the teams’ findings.
The research team identified three variants within the speculative execution research. The below grid details the specific variants detailed in the research and the AMD response details.”
ARM
In a comment given to Wired, ARM’s Public relations director Phil Hughes said, "I can confirm that Arm have been working together with Intel and AMD to address a side-channel analysis method which exploits speculative execution techniques used in certain high-end processors, including some of our Cortex-A processors. This method requires malware running locally and could result in data being accessed from privileged memory." Hughes also said that ARM's IoT-focused Cortex-M line is not affected by the bug.
Apple
“Apple has already released mitigations in iOS 11.2, macOS 10.13.2, and tvOS 11.2 to help defend against Meltdown. Apple Watch is not affected by Meltdown. In the coming days we plan to release mitigations in Safari to help defend against Spectre. We continue to develop and test further mitigations for these issues and will release them in upcoming updates of iOS, macOS, tvOS, and watchOS”
So, just download the latest macOS version to be safe. You can read the full statement here
Microsoft
The latest security patch is available via a Windows update. Look for the KB4054022 patch. It is being rolled out automatically, but you can download the patch from here. Anyway, this is what Microsoft said –
“We're aware of this industry-wide issue and have been working closely with chip manufacturers to develop and test mitigations to protect our customers. We are in the process of deploying mitigations to cloud services and have also released security updates to protect Windows customers against vulnerabilities affecting supported hardware chips from Intel, ARM, and AMD. We have not received any information to indicate that these vulnerabilities had been used to attack our customers.”
Via Verge
Linux (Ubuntu)
While there are plenty of Linux distros out there, Ubuntu remains one of the most popular distros used by both consumer and commercial customers. The patch to resolve Meltdown issue is out via Kernel update and you can go check out respective linux Distro page to know more. Here is what it had to say.
“It was discovered that a new class of side channel attacks impact most processors, including processors from Intel, AMD, and ARM. The attack allows malicious userspace processes to read kernel memory and malicious code in guests to read hypervisor memory. To address the issue, updates to the Ubuntu kernel and processor microcode will be needed. These updates will be announced in future Ubuntu Security Notices once they are available.”
The post also says, “The original coordinated disclosure date was planned for January 9 and we have been driving toward that date to release fixes. Due to the early disclosure, we are trying to accelerate the release, but we don't yet have an earlier ETA when the updates will be released. We will release Ubuntu Security Notices when the updates are available.”
You can read the full statement here
In addition, various anti-virus software makers are also working on adding the issue into their bug list and patching it through their end.
Don’t Panic, the issue might not rob your PC of its performance
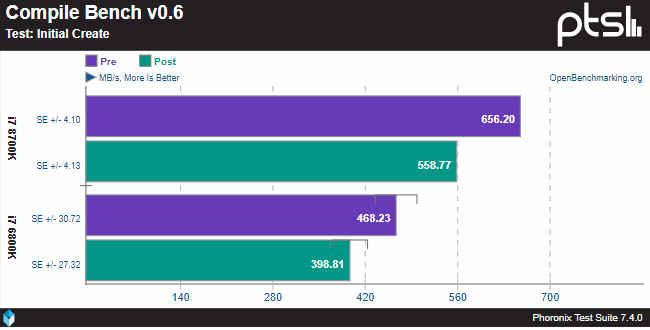
It was also reported that to resolve the issue, running processes and Kernel page will be kept completely separate. Termed as KPTI patch on the Linux side, this will essentially increase the Kernel’s overhead which will slow down the computer. Reports say that Intel processors will see a performance drop of 0-30 percent. However, initial testing done by Hardware Unboxed suggest that there is no discernible change in performance. The results seem to concur with Phoronix’s game testing results on Linux 4.15. These results may stand for newer Intel processors as well. However, we are yet to see results from older processors. That said, the preliminary results look promising.
The server side of things aren’t that great though
Sadly, the performance drop might be a real issue for system running virtualised environments, such as Cloud services. A software developer blogging as Python Sweetness wrote on his post,
“There is presently an embargoed security bug impacting apparently all contemporary CPU architectures that implement virtual memory, requiring hardware changes to fully resolve. Urgent development of a software mitigation is being done in the open and recently landed in the Linux kernel, and a similar mitigation began appearing in NT kernels in November. In the worst case the software fix causes huge slowdowns in typical workloads. There are hints the attack impacts common virtualization environments including Amazon EC2 and Google Compute Engine.”
AWS (Amazon Web Services) and Microsoft's Azure Cloud which hold data servers for a variety of services will go into maintenance starting this weekend. Both services rely heavily on Intel powered CPUs and are powered by both Linux and Microsoft OS platforms.
Phoronix also reported yesterday that there is a definite drop in performance here. The initial tests were performed on Intel Core i7-8700K, which is consumer grade chip. However, we may see newer results come in later this month once people start testing the new update on server Xeon processors.
What a mess!
There is a lesson to be learnt in all this and whether someone takes responsibility or not for what has happened, we need to take a long hard look at what has been happening.
Linux creator Linus Trovalds had a very harsh response to this Intel’s mess. He said, “I think somebody inside of Intel needs to really take a long hard look at their CPU’s, and actually admit that they have issues instead of writing PR blurbs that say that everything works as designed.” He added, “And that really means that all these mitigation patches should be written with ‘not all CPU’s are crap’ in mind. Or is Intel basically saying ‘We are committed to selling you shit forever and ever, and never fixing anything? Because if that’s the case, maybe we should start looking towards the ARM64 people more.”
On a more realistic note, this is what researchers had to say at the end of the Spectre paper.
“The vulnerabilities in this paper, as well as many others, arise from a longstanding focus in the technology industry on maximizing performance. As a result, processors, compilers, device drivers, operating systems, and numerous other critical components have evolved compounding layers of complex optimizations that introduce security risks. As the costs of insecurity rise, these design choices need to be revisited, and in many cases alternate implementations optimized for security will be required.”
Hardik Singh
Light at the top, this odd looking creature lives under the heavy medication of video games. View Full Profile